
by Deep Green Resistance News Service | Nov 24, 2018 | Strategy & Analysis
Editor’s note: The following is from the chapter “Tactics and Targets” of the book Deep Green Resistance: A Strategy to Save the Planet. This book is now available for free online.
by Aric McBay
A good tactic used on a poor target has little effect.
The Field Manual on Guerrilla Warfare identifies four “important factors related to the target which influence its final selection,”10 later expanded to six with the CARVER matrix.13 These criteria are meant specifically for targets to be disrupted or destroyed, not necessarily when choosing potential targets for intelligence gathering or further investigation. The six criteria are as follows:
Criticality. How important is this target to the enemy and to enemy operations? “A target is critical when its destruction or damage will exercise a significant influence upon the enemy’s ability to conduct or support operations. Such targets as bridges, tunnels, ravines, and mountain passes are critical to lines of communication; engines, ties, and POL [petroleum, oil, and lubricant] stores are critical to transportation. Each target is considered in relationship to other elements of the target system.” Resistance movements (and the military) look for bottlenecks when selecting a target. And they make sure to think in big picture terms, rather than just in terms of a specific individual target. What target(s) can be disrupted or destroyed to cause maximum damage to the entire enemy system? Multiple concurrent surprise attacks are ideal for resistance movements, and can cause cascading failures.
Accessibility. How easy is it to get near the target? “Accessibility is measured by the ability of the attacker to infiltrate into the target area. In studying a target for accessibility, security controls around the target area, location of the target, and means of infiltration are considered.” It’s important to make a clear distinction between accessibility and vulnerability. For a resister in Occupied France, a well-guarded fuel depot might be explosively vulnerable, but not very accessible. For resisters in German-occupied Warsaw, the heavy wall surrounding the Warsaw Ghetto might be easily accessible, but not very vulnerable unless they carried powerful explosives. Good intelligence and reconnaissance are key to identifying and bypassing obstacles to access.
Recuperability. How much effort would it take to rebuild or replace the target? “Recuperability is the enemy’s ability to restore a damaged facility to normal operating capacity. It is affected by the enemy capability to repair and replace damaged portions of the target.” Specialized installations, hard-to-find parts, or people with special unique skills are difficult to replace. Targets with very common or mass-produced and stockpiled components would be poorer targets in terms of recuperability. Undermining enemy recuperability can be done with good planning and multiple attacks: SOE saboteurs were trained to target the same important parts on every machine. If they were to sabotage all of the locomotives in a stockyard, they would blow up the same part on each train, thus preventing the engineers from cannibalizing parts from other trains to make a working one.
Vulnerability. How tough is the target? “Vulnerability is a target’s susceptibility to attack by means available to [resistance] forces. Vulnerability is influenced by the nature of the target, i.e., type, size, disposition and composition.” In military terminology, a “soft target” is one that is relatively vulnerable, while a “hard target” is well defended or fortified. A soft target could be a sensitive electrical component, a flammable storage shed, or a person. A hard target might be a roadway, a concrete bunker, or a military installation. Hard targets require more capacity or armament to disable. A battle tank might have lower vulnerability when faced with a resister armed with a Molotov cocktail, but high vulnerability against someone armed with a rocket-propelled grenade.
Effect. Will a successful attack increase the chances of achieving larger goals? What consequences might result, intended and unintended? An attack on a pipeline might result in an oil spill, with collateral damage to life in the immediate vicinity. Escalation of sabotage might result in increased surveillance and repression of the general populace.
Recognizability. How difficult is it to identify the target during the operation, under different conditions of daylight, weather, and season? A brightly lit facility adjacent to a road is easy to locate, even at night, but it may be difficult to pick out a particular oil derrick owned by a particular company amidst acres of wells, or a specific CEO in a crowd of businesspeople.
From this perspective the ideal target would be highly critical (such that damage would cause cascading systems failures), highly vulnerable, very accessible and easy to identify, difficult and time-consuming to repair or replace, and unlikely to cause undesirable side effects. The poorest target would be of low importance for enemy operations but with high risk of negative side effects, hardened, inaccessible and hard to find, and easily replaced. You’ll note that there’s no category for “symbolic value” to the enemy, because the writers of the manual weren’t interested in symbolic targets. They consistently emphasize that successful operations will undermine the morale of the adversary, while increasing morale of the resisters and their supporters. The point is to carry out decisively effective action with the knowledge that such action will have emotional benefits for your side, not to carry out operations that seem emotionally appealing in the hopes that those choices will lead to effective action.
An additional criterion not discussed above would be destructivity. How damaging is the existence of the target to people and other living creatures? A natural gas–burning power plant might be more valuable based on the six criteria, but a coal-fired power plant could be more destructive, making it a higher priority from a practical and symbolic perspective.
It’s rare to find a perfect target. It’s more likely that choosing among targets will require certain trade-offs. A remote enemy installation might be more vulnerable, but it could also be more difficult to access and possibly less important to the adversary. Larger, more critical installations are often better guarded and less vulnerable. Target decisions have to be made in the context of the larger strategy, taking into account tactics and organizational capability.
One of the reasons that the Earth Liberation Front (ELF) has had limited decisive success so far is that its targets have had low criticality and high recuperability. New suburban subdivisions are certainly crimes against ecology, but partially constructed homes are not very important to those in power, and they are relatively replaceable. The effect is primarily symbolic, and it’s hard to find a case in which a construction project has actually been given up because of ELF activity—although many have certainly been made more expensive.
Most often, it seems that resistance targets in North America are chosen on the basis of vulnerability and accessibility, rather than on criticality. It’s easy to walk up to a Walmart window and smash it in the middle of the night or to destroy a Foot Locker storefront during a protest march. Aggressive symbolic attacks do get attention, and if a person’s main indicator of success is a furor on the 10:00 pm news, then igniting the local Burger King is likely to achieve that. But making a decisive impact on systems of power and their basis of support is more difficult to measure. If those in power are clever, they’ll downplay the really damaging actions to make themselves seem invulnerable, but scream bloody murder over a smashed window in order to whip up public opinion. And isn’t that what often happens on the news? If a biotech office is smashed and not a single person injured, the corporate journalists and pundits start pontificating about “violence” and “terrorism.” But if a dozen US soldiers are blown up by insurgents in Iraq, the White House press secretary will calmly repeat over and over that “America” is winning and that these incidents are only minor setbacks.
The Black Liberation Army (BLA) is an example of a group that chose targets in alignment with its goals. The BLA formed as an offshoot (or, some would argue, as a parallel development) of the Black Panther Party. The BLA was not interested in symbolic targets, but in directly targeting those who oppressed people of color. Writes historian Dan Berger: “The BLA’s Program included three components: retaliation against police violence in Black communities; elimination of drugs and drug dealers from Black communities; and helping captured BLA members escape from prison.”11 The BLA essentially believed that aboveground black organizing was doomed because of violent COINTELPRO-style tactics, and that the BPP had become a reformist organization. They argued that “the character of reformism is based on unprincipled class collaboration with our enemy.”12 In part because of their direct personal experience of violent repression at the hands of the state, they did not hesitate to kill white police officers in retaliation for attacks on the black community.
The IRA was also ruthless in their target selection, though they had limited choices in terms of attacking their occupiers. By the time WWII rolled around, resisters in Europe had a wide variety of potential and critical targets for sabotage, such as rail and telegraph lines, and further industrialization has only increased the number of critical mechanical targets, but a century ago, Ireland was hardly mechanized at all. That is why Michael Collins correctly identified British intelligence agents as the most critical and least recuperable targets available. Furthermore, his networks of spies and assassins made those agents—already soft targets—highly accessible. They were a perfect match for all six target selection criteria.
It’s worth noting that these six criteria are not just applicable to targets that are going to be destroyed. The same criteria are used to select “pressure points” on which to exert political force for any strategy of resistance, even one that is explicitly nonviolent. Effective strikes or acts of civil disobedience can exert more political force by disrupting more critical and vulnerable targets—the more accessible, the better.
These criteria for target selection go both ways. Our own resistance movements are targets for those in power, and it’s important to understand our organizations as potential targets. Leaders have often been attacked because they were crucial to the organization. Underground leaders are less accessible, but potentially more vulnerable if they can be isolated from their base of support. And aboveground groups often have better recuperability, because they have a larger pool to draw from and fewer training requirements; recall the waves after waves of civil rights activists willing to be arrested in Birmingham, Alabama.
Anyone who casts their lot with a resistance movement must be prepared for reprisals. Those reprisals will come whether the actionists are aboveground or underground, choosing violence or nonviolence. Many activists, especially from privileged backgrounds, naïvely assume that fighting fair will somehow cause those in power to do the same. Nothing could be further from the truth. The moment that any power structure feels threatened, it will retaliate. It will torture Buddhists and nuns, turn fire hoses on school children, and kill innocent civilians. A brief perusal of Amnesty International’s website will acquaint you with nonviolent protestors around the globe currently being detained and tortured or who have disappeared for simple actions like letter writing or peaceably demonstrating.
This is a reality that privileged people must come to terms with or else any movement risks a rupture when power comes down on actionists. Those retaliations are not anyone’s fault; they are to be expected. Any serious resistance movement should be intellectually and emotionally prepared for the power structure’s response. People are arrested, detained, and killed—often in large numbers—when power strikes back. Those who provide a challenge to power will be faced with consequences, some of them inhumanly cruel. The sooner everyone understands that, the better prepared we all will be to handle it.

Now, having discussed what makes good strategy, how resistance groups organize effectively, and what sort of culture resistance groups need to support them, it is time to take a deep breath. A real deep breath.
This culture is killing the planet. It systematically dispossesses sustainable indigenous cultures. Runaway global warming (and other toxic effects of this culture) could easily lead to billions of human deaths, and indeed the murder of the oceans, and even more, the effective destruction of this planet’s capacity to support life.
The question becomes: what is to be done?

by Deep Green Resistance News Service | Nov 23, 2018 | Strategy & Analysis
by Max Wilbert / Deep Green Resistance
We live inside an unprecedented surveillance state. Government and corporations monitor all non-encrypted digital communications for the purposes of political control and profit.
Political dissidents who wish to challenge capitalism need to learn to use more secure methods for communication, research, and other digital tasks. This guide is aimed at serious dissidents and revolutionaries. It is not aimed at the everyday activist, who will likely find these practices to be overkill.
Privacy vs. Security
It is important to understand that privacy and security are two different things. Privacy is related to anonymity. Security protects from eavesdropping, but does not necessarily anonymize.
To use an analogy: privacy means that the government doesn’t know who sent the message, but can read the contents. Security means they know who sent the message, but cannot read it. This is a simplified understanding, but it’s important to distinguish between the two.
In general, most aboveground activists who are already operating in the public sphere prioritize security. Underground operators and revolutionaries generally prioritize anonymity, since being unmasked and identified is the primary danger. Of course, this is a generalization. Both security and privacy are important for anyone involved in anti-capitalist resistance.
Note that these tools require some relatively advanced technological skills. However, it’s worth learning to use these tools. Whonix is probably the easiest to use for a beginner.
Operating Systems
An operating system, or OS, is the basic software running on a computing device. Windows and Mac OS are the most common operating systems. However, Linux is the most secure family of operating systems. This guide will look at operating systems for desktop computer use.
The following information is copied from the websites for these projects.
TAILS
Tails is a live system that aims to preserve your privacy and anonymity. It helps you to use the Internet anonymously and circumvent censorship almost anywhere you go and on any computer but leaving no trace unless you ask it to explicitly.
It is a complete operating system designed to be used from a USB stick or a DVD independently of the computer’s original operating system. It is Free Software and based on Debian GNU/Linux.
Tails comes with several built-in applications pre-configured with security in mind: web browser, instant messaging client, email client, office suite, image and sound editor, etc.
Tails relies on the Tor anonymity network to protect your privacy online:
- all software is configured to connect to the Internet through Tor
- if an application tries to connect to the Internet directly, the connection is automatically blocked for security.
Tor is an open and distributed network that helps defend against traffic analysis, a form of network surveillance that threatens personal freedom and privacy, confidential business activities and relationships, and state security.
Tor protects you by bouncing your communications around a network of relays run by volunteers all around the world: it prevents somebody watching your Internet connection from learning what sites you visit, and it prevents the sites you visit from learning your physical location.
Using Tor you can:
- be anonymous online by hiding your location,
- connect to services that would be censored otherwise;
- resist attacks that block the usage of Tor using circumvention tools such as bridges.
To learn more about Tor, see the official Tor website, particularly the following pages:
- Tor overview: Why we need Tor
- Tor overview: How does Tor work
- Who uses Tor?
- Understanding and Using Tor — An Introduction for the Layman
Using Tails on a computer doesn’t alter or depend on the operating system installed on it. So you can use it in the same way on your computer, a friend’s computer, or one at your local library. After shutting down Tails, the computer will start again with its usual operating system.
Tails is configured with special care to not use the computer’s hard-disks, even if there is some swap space on them. The only storage space used by Tails is in RAM, which is automatically erased when the computer shuts down. So you won’t leave any trace on the computer either of the Tails system itself or what you used it for. That’s why we call Tails “amnesic”.
This allows you to work with sensitive documents on any computer and protects you from data recovery after shutdown. Of course, you can still explicitly save specific documents to another USB stick or external hard-disk and take them away for future use.
https://tails.boum.org/
Whonix
Whonix is a desktop operating system designed for advanced security and privacy. Whonix mitigates the threat of common attack vectors while maintaining usability. Online anonymity is realized via fail-safe, automatic, and desktop-wide use of the Tor network. A heavily reconfigured Debian base is run inside multiple virtual machines, providing a substantial layer of protection from malware and IP address leaks. Commonly used applications are pre-installed and safely pre-configured for immediate use. The user is not jeopardized by installing additional applications or personalizing the desktop. Whonix is under active development and is the only operating system designed to be run inside a VM and paired with Tor.
Whonix utilizes Tor’s free software, which provides an open and distributed relay network to defend against network surveillance. Connections through Tor are enforced. DNS leaks are impossible, and even malware with root privileges cannot discover the user’s real IP address. Whonix is available for all major operating systems. Most commonly used applications are compatible with the Whonix design.
https://www.whonix.org/
Qubes OS
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are Microsoft Windows, Mac OS X, Android, and iOS. Qubes is free and open-source software (FOSS). This means that everyone is free to use, copy, and change the software in any way. It also means that the source code is openly available so others can contribute to and audit it.
Why is OS security important?
Most people use an operating system like Windows or OS X on their desktop and laptop computers. These OSes are popular because they tend to be easy to use and usually come pre-installed on the computers people buy. However, they present problems when it comes to security. For example, you might open an innocent-looking email attachment or website, not realizing that you’re actually allowing malware (malicious software) to run on your computer. Depending on what kind of malware it is, it might do anything from showing you unwanted advertisements to logging your keystrokes to taking over your entire computer. This could jeopardize all the information stored on or accessed by this computer, such as health records, confidential communications, or thoughts written in a private journal. Malware can also interfere with the activities you perform with your computer. For example, if you use your computer to conduct financial transactions, the malware might allow its creator to make fraudulent transactions in your name.
Aren’t antivirus programs and firewalls enough?
Unfortunately, conventional security approaches like antivirus programs and (software and/or hardware) firewalls are no longer enough to keep out sophisticated attackers. For example, nowadays it’s common for malware creators to check to see if their malware is recognized by any signature-based antivirus programs. If it’s recognized, they scramble their code until it’s no longer recognizable by the antivirus programs, then send it out. The best of these programs will subsequently get updated once the antivirus programmers discover the new threat, but this usually occurs at least a few days after the new attacks start to appear in the wild. By then, it’s too late for those who have already been compromised. More advanced antivirus software may perform better in this regard, but it’s still limited to a detection-based approach. New zero-day vulnerabilities are constantly being discovered in the common software we all use, such as our web browsers, and no antivirus program or firewall can prevent all of these vulnerabilities from being exploited.
How does Qubes OS provide security?
Qubes takes an approach called security by compartmentalization, which allows you to compartmentalize the various parts of your digital life into securely isolated compartments called qubes.
This approach allows you to keep the different things you do on your computer securely separated from each other in isolated qubes so that one qube getting compromised won’t affect the others. For example, you might have one qube for visiting untrusted websites and a different qube for doing online banking. This way, if your untrusted browsing qube gets compromised by a malware-laden website, your online banking activities won’t be at risk. Similarly, if you’re concerned about malicious email attachments, Qubes can make it so that every attachment gets opened in its own single-use disposable qube. In this way, Qubes allows you to do everything on the same physical computer without having to worry about a single successful cyberattack taking down your entire digital life in one fell swoop.
Moreover, all of these isolated qubes are integrated into a single, usable system. Programs are isolated in their own separate qubes, but all windows are displayed in a single, unified desktop environment with unforgeable colored window borders so that you can easily identify windows from different security levels. Common attack vectors like network cards and USB controllers are isolated in their own hardware qubes while their functionality is preserved through secure networking, firewalls, and USB device management. Integrated file and clipboard copy and paste operations make it easy to work across various qubes without compromising security. The innovative Template system separates software installation from software use, allowing qubes to share a root filesystem without sacrificing security (and saving disk space, to boot). Qubes even allows you to sanitize PDFs and images in a few clicks. Users concerned about privacy will appreciate the integration of Whonix with Qubes, which makes it easy to use Tor securely, while those concerned about physical hardware attacks will benefit from Anti Evil Maid.
How does Qubes OS compare to using a “live CD” OS?
Booting your computer from a live CD (or DVD) when you need to perform sensitive activities can certainly be more secure than simply using your main OS, but this method still preserves many of the risks of conventional OSes. For example, popular live OSes (such as Tails and other Linux distributions) are still monolithic in the sense that all software is still running in the same OS. This means, once again, that if your session is compromised, then all the data and activities performed within that same session are also potentially compromised.
How does Qubes OS compare to running VMs in a conventional OS?
Not all virtual machine software is equal when it comes to security. You may have used or heard of VMs in relation to software like VirtualBox or VMware Workstation. These are known as “Type 2” or “hosted” hypervisors. (The hypervisor is the software, firmware, or hardware that creates and runs virtual machines.) These programs are popular because they’re designed primarily to be easy to use and run under popular OSes like Windows (which is called the host OS, since it “hosts” the VMs). However, the fact that Type 2 hypervisors run under the host OS means that they’re really only as secure as the host OS itself. If the host OS is ever compromised, then any VMs it hosts are also effectively compromised.
By contrast, Qubes uses a “Type 1” or “bare metal” hypervisor called Xen. Instead of running inside an OS, Type 1 hypervisors run directly on the “bare metal” of the hardware. This means that an attacker must be capable of subverting the hypervisor itself in order to compromise the entire system, which is vastly more difficult.
Qubes makes it so that multiple VMs running under a Type 1 hypervisor can be securely used as an integrated OS. For example, it puts all of your application windows on the same desktop with special colored borders indicating the trust levels of their respective VMs. It also allows for things like secure copy/paste operations between VMs, securely copying and transferring files between VMs, and secure networking between VMs and the Internet.
How does Qubes OS compare to using a separate physical machine?
Using a separate physical computer for sensitive activities can certainly be more secure than using one computer with a conventional OS for everything, but there are still risks to consider. Briefly, here are some of the main pros and cons of this approach relative to Qubes:
Pros
- Physical separation doesn’t rely on a hypervisor. (It’s very unlikely that an attacker will break out of Qubes’ hypervisor, but if one were to manage to do so, one could potentially gain control over the entire system.)
- Physical separation can be a natural complement to physical security. (For example, you might find it natural to lock your secure laptop in a safe when you take your unsecure laptop out with you.)
Cons
- Physical separation can be cumbersome and expensive, since we may have to obtain and set up a separate physical machine for each security level we need.
- There’s generally no secure way to transfer data between physically separate computers running conventional OSes. (Qubes has a secure inter-VM file transfer system to handle this.)
- Physically separate computers running conventional OSes are still independently vulnerable to most conventional attacks due to their monolithic nature.
- Malware which can bridge air gaps has existed for several years now and is becoming increasingly common.
(For more on this topic, please see the paper Software compartmentalization vs. physical separation.)
Get Qubes
Qubes OS is free to use, can run , and integrates with Whonix for secure web browsing and internet usage via Tor.
https://www.qubes-os.org/
Summary
- TAILS is a “live” OS that runs from a USB stick or DVD, and can be used to browse anonymously from any computer. It doesn’t save files or history; it is designed mainly for ephemeral use.
- Whonix is an OS made to run as a virtual machine, and provide security and anonymity for web browsing by routing all connections via the Tor browser.
- Qubes OS is made to use as a permanent OS, and uses compartmentalization for security. Whonix is automatically installed inside Qubes. Used by Edward Snowden.
Image: Chris, https://www.flickr.com/photos/44730926@N07/32681532676, CC BY 2.0

by DGR News Service | Nov 21, 2018 | The Problem: Civilization
Editor’s note: We live in a world on the brink. As the climate crisis intensifies, racism and patriarchy rise and corporate control expands. What can be done? We Choose to Speak features a collection of essays by writer and organizer Max Wilbert exploring these topics and their solutions.
by Max Wilbert / Deep Green Resistance
The United States is a military empire that was built and is maintained by organized violence.
The origins of this country lie with the military conquest and either destruction or forced resettlement of indigenous people. Today, the modern American lifestyle is maintained, as Thomas Friedman (someone with whom I agree on very little) writes, by the “hidden fist” of the military.
“McDonalds cannot flourish without MacDonald Douglass,” Friedman wrote. “And the hidden fist that keeps the world safe for Silicon Valley’s technologies to flourish is called the US Army, Air Force, Navy, and Marine Corps.”
I am reminded of this fact every August. August brings Seafair to Seattle, and with Seafair comes the Blue Angels, a Navy/Marines squadron of F/A-18 fighter bombers that travels the US each year, entertaining the public for an annual cost of $37 million.
As these jet aircraft roar overhead, I cover my ears and wince at the spectacle of widespread public adulation. These war machines are worshipped. Earlier today, I watched a five-year-old boy cheering and yelling “yee-haw” as the fighter formation shot overhead. Out on Lake Washington, a toxified remnant of what was once an ecological paradise, other Seattle residents on boats and rafts raised their hands towards the jets in supplication. As five aircraft passed directly overhead, I watched one white American man hold a can of beer above his face and pour the liquid directly down his throat.
For thousands of people, the roar of an F/A-18 fighter bomber is the last sound they ever heard. The F/A-18 aircraft played a major role during the 2001 US invasion of Afghanistan and the 2003 US invasion of Iraq. Between these two conflicts, more than a million civilians were killed—many of them in bombings. The same jet continues to be used in Syria, in Yemen, in Somalia, and elsewhere all around the world.
The US military uses its power to promote and protect a certain vision of prosperity and societal development. In 1948, George Kennan, then the Director of Policy Planning for the US State Department, wrote in Memo PPS23 that “[The United States has] about 50 percent of the world’s wealth but only 6.3 percent of its population… Our real task in the coming period is to devise a pattern of relationships, which will permit us to maintain this position of disparity…”
In the 70 years since Kennan wrote that memo, that “pattern of relationships” has been successfully devised and maintained. The US military is the largest in the world by expenditure, with more than $600 billion in annual funding and more than 2 million personnel (including reservists).
The true costs of this are incalculable. They range from the ecocidal, genocidal destruction of Vietnam and Cambodia to the horrors of Gulf War Syndrome to the toxic remnants of weapons manufactories in cities across the country. In Guatemala and El Salvador, the legacy of US-sponsored right-wing terrorism still echoes through a shattered society. In Nevada and across oceania, indigenous lands remain irradiated from decades of weapons testing, and nuclear waste which continues to leak into groundwater and seep into soils will remain deadly for hundreds of thousands of years.
As Friedman reminds us, military might and corporate power remain inextricably linked in creating consumer culture. We are reminded of this at Seafair, where sponsors include 76, Boeing, Starbucks, Amazon, Uber, Oracle, Microsoft, LG, Samsung, CapitalOne, and many others.
Each F/A-18 costs about $29 million, and is produced by Boeing, the second-largest weapons manufacturer in the world, one of the 100 largest companies in the world, with just under $100 billion in annual revenue. Seattle still fawns over Boeing, which brought so much wealth to this region, just as it now fawns over Amazon and Microsoft. Their digital products colonize our minds, just as Boeing’s weapons help control territory.
Seafair also includes public tours of two warships, the USS Momsen (an Arleigh Burke-class guided missile destroyer equipped with 96 missiles) and the USS Somerset (a $2 billion troop transport ship equipped to carry 600+ soldiers and vehicles into combat zones). As thousands of people file through the ships, exclaiming over the might of the empire, we must remember that the US military is also the single largest polluter in the world, responsible for more greenhouse gas emissions than any other single entity.
Some people think that because I critique the US military and US empire, I must support this nation’s opponents. This logic is absurd. The Taliban and ISIS, the Nazi regime, the Stalinist Soviet state; US enemies have included countless reprehensible regimes. Repression must be fought, but this nation always has ulterior motives hidden behind humanitarian rhetoric. In the games of empire, the people and the planet are being sacrificed.
Our enemy is empire itself.
But despite my opposition to imperialist wars, I’m not a pacifist. A friend of mine, Vince Emanuele, served in the Marine Corps during the invasion of Iraq. He became disillusioned with the military, left the service, and became a leading voice of dissent against the war.
In the wake of one of the latest calls for mass regulation of firearms, he wrote:
“Sure, I’ll give up my guns, as soon as the NSA, CIA, FBI, DEA, ATF, police, military, and right-wing militias disarm themselves. Until then, my liberal, progressive, and “leftist” friends can eat tofu, watch MSNBC/Bill Moyers, and go fly a kite. Your collective commentary is akin to the “privileged white-classes” that you so often rail against.
Believe me, I’d love to live in a world without guns, violence, and so forth. But, I’m not naive enough to believe these things are going away anytime soon. This nation is extremely sick, twisted, undereducated, and plagued with an exploding prison population, growing inequality, and ever-expanding military empire and surveillance state. We should be expecting much more violence in the future, not less.
Clearly, within the context of rapid climate change, growing social ills, and a collapsing economic system, giving up your weaponry seems a bit insane and utterly naive. Interestingly, it’s the liberals and progressives, who’ve largely grown up in cosmopolitan/suburban areas, who sound like the spoiled little American brats we so often challenge.
If you’ve never carried, fired, cleaned, taken apart, or counted on a weapon to save your life, I suggest taking a more humble approach to this issue. Conversely, if you’ve only fired your daddy’s handgun, shotgun, and rifle in the backyard, I suggest scaling back the glorification of weapons and violence.
If I thought killing and warfare were fun, I would have stayed in the military–but I didn’t. If I though weapons were unnecessary, I wouldn’t own any–but I do.”
Perhaps it’s time for a people’s army—a left-wing guerilla force, grounded in feminism, anti-racism, and respect for human rights—to fight back against the imperialist empire, to bring the fight home and make CEOs and corporations and right-wing neofascists afraid again.
Interested readers can check out this and other radical books at BabylonApocalypse.org

by Deep Green Resistance News Service | Nov 14, 2018 | Music & Art
by Max Wilbert / Deep Green Resistance
“And for destroying the destroyers of the earth…” — Revelations, 11-18
The film “First Reformed” has an interesting premise. Toller (Ethan Hawke) is the sad, solitary pastor of a small church who is asked to help Michael (Philip Ettinger), an activist and member of his congregation, who is struggling.
The two begin a dialogue, and Michael shares a sense of hopelessness in the face of ecological collapse. “It’s 2017,” he says, “and the IPCC said in 2010 that if drastic changes weren’t made by 2015, the entire planet’s ecology might collapse.” He also points out that hundreds of environmental activists are killed worldwide every year.
As Toller grapples with the existential questions brought on by this conversation, Michael’s wife Mary (played by Amanda Seyfried) finds explosives and a suicide vest hidden in the garage, and shows them to Toller, who takes them away. After discovering that his stash gone, Michael commits suicide.
The first major flaw in the film is the perpetuation of the stereotype that being aware of the state of the planet—toxification, species extinction, global warming, the refugee crisis, etc.—is to be consumed by all-encompassing depression. Michael is also described as having “no friends” and being “barely even sociable.”
These ideas are inaccurate and dangerous. The key message is this: if contemplating ecological collapse will drive you to suicide, then the science and discourse around ecological collapse is dangerous and should be avoided at all costs. This idea strengthens and validates the culture of denial that dominates popular discourse, and the stereotype that revolutionaries are depressed and alone.
In my experience, the opposite is true: those of us who fight back have rich communities and better mental health than the average. These themes resurface later in the film as well.
Toller is left to provide some small support to Mary, now a widow. But he remains deeply troubled by the statistics and trends on ecological collapse that the film accurately depicts.
The film sets up a tension between Toller’s small, struggling church and a massive nearby congregation—generously funded by a large fossil fuel corporation. The subtext is clear, and meant to examine the tension between religion at its best, as a source of moral guidance and inspiration for freedom fighters such as those on the underground railroad, and at its worst, as a narcotic, as the opiate of the masses and a tool of colonization.
At this point in the film, Toller’s simmering rage, sadness, and emotion waiting to explode become more apparent. Hidden beneath the puritan veneer of a small-town preacher lies alcoholism and a deep sadness. “No sooner do I close my eyes than desolation is upon me,” he says at one point in the film, after recounting the death of his son in Iraq—a war he encouraged his son to join, then later came to see as unjust.
After a promising start, the film takes a nosedive. There are two points on which the ending of the film fails completely. The first is feminist, the second environmental.
I thought, at first, naively, that this film wasn’t going to fall into casting the female lead as a sex object. But, predictably, it did, in a strange scene in which Mary, who is presumed to be in her early 30’s and who is pregnant and recently widowed, asks Toller, in his late 40’s, alcoholic and a minister, to snuggle with her. However, the scene seems to remain platonic, despite its strangeness and improbability.
After this, tortured by the thought of environmental collapse and by the collaboration between the oil company and his fellow Christians, Hawke decides to take the suicide vest (which he has kept) into a public event and blow himself—and the oil executives—up. After seeing Mary unexpectedly arrive, he doffs the explosives, wraps himself in rusty barbed wire, and prepares to commit suicide himself by drinking drain cleaner. Then Mary comes into the room, her and Toller begin kissing, and film ends abruptly.
What the fuck?
This is why I hate Hollywood and don’t really watch movies. Provided with a fascinating topic and a talented cast, all the filmmaker can muster is this emotional trainwreck, this pointlessness.
As is so common in popular culture, the artist (the director, in this case) confuses emotional turmoil with deep meaning. The final message might as well be a line Toller reads from his bible: “…the knowledge of the emptiness of all things, which can only be filled by the knowledge of our savior.”
Both of Toller’s final approaches—the suicide vest and the barbed wire—represent the self-flagellation of total helplessness. They are only personal solutions, not social or moral or political ones.
Revolutionaries don’t need this shit. We need cultural products—art, music, film, books, poetry, etc.—which nurture our resistance spirit, encourage our hearts, and teach us about healthy lives and effective ways of fighting empire.
Don’t waste your time on this film, or any other bullshit coming out of Hollywood.

by Deep Green Resistance News Service | Nov 11, 2018 | Strategy & Analysis
Featured image: power line sabotaged by the African National Congress
Editor’s note: The following is from the chapter “Tactics and Targets” of the book Deep Green Resistance: A Strategy to Save the Planet. This book is now available for free online.
by Aric McBay
Some tactics can be carried out underground—like general liberation organizing and propaganda—but are more effective aboveground. Where open speech is dangerous, these types of tactics may move underground to adapt to circumstances. The African National Congress, in its struggle for basic human rights, should have been allowed to work aboveground, but that simply wasn’t possible in repressive apartheid South Africa.
And then there are tactics that are only appropriate for the underground, obligate underground operations that depend on secrecy and security. Escape lines and safehouses for persecuted persons and resistance fugitives are example of those operations. There’s a reason it’s called the “underground” railroad—it’s not transferable to the aboveground, because the entire operation is completely dependent on secrecy. Clandestine intelligence gathering is another case; the French Resistance didn’t gather enemy secrets by walking up to the nearest SS office and asking for a list of their troop deployments.
Some tactics are almost always limited to the underground:
- Clandestine intelligence
- Escape
- Sabotage and attacks on materiel
- Attacks on troops
- Intimidation
- Assassination
As operational categories, intelligence and escape are pretty clear, and few people looking at historical struggles will deny the importance of gathering information or aiding people to escape persecution. Of course, some abolitionists in the antebellum US didn’t support the Underground Railroad. And many Jewish authorities tried to make German Jews cooperate with registration and population control measures. In hindsight, it’s clear to us that these were huge strategic and moral mistakes, but at the time it may only have been clear to the particularly perceptive and farsighted.
Sabotage and attacks on materiel are overlapping tactics. Oftentimes, sabotage is more subtle; for example, machinery may be disabled without being recognized as sabotage. Attacks on materiel are often more overt efforts to destroy and disable the adversary’s equipment and supplies. In any case, they form an inclusive continuum, with sabotage on the more clandestine end of the scale.
It’s true that harm can be caused through sabotage, and that sabotage can be a form of violence. But allowing a machine to operate can also be more violent than sabotaging it. Think of a drift net. How many living creatures does a drift net kill as it passes through the ocean, regardless of whether it’s being used for fishing or not? Destroying a drift net—or sabotaging a boat so that a drift net cannot be deployed—would save countless lives. Sabotaging a drift net is clearly a nonviolent act. However, you could argue conversely that not sabotaging a drift net (provided you had the means and opportunity) is a profoundly violent act—indeed, violent not just for individual creatures, but violent on a massive, ecological scale. The drift net is an obvious example, but we could make a similar (if longer and more roundabout) argument for most any industrial machinery.
You’re opposed to violence? So where’s your monkey wrench?
Sabotage is not categorically violent, but the next few underground categories may involve violence on the part of resisters. Attacks on troops, intimidation, assassination, and the like have been used to great effect by a great many resistance movements in history. From the assassination of SS officers by escaping concentration camp inmates to the killing of slave owners by revolting slaves to the assassination of British torturers by Michael Collins’s Twelve Apostles, the selective use of violence has been essential for victory in a great many resistance and liberation struggles.
Attacks on troops are common where a politically conscious population lives under overt military occupation. In these situations, there is often little distinction between uniformed militaries, police, and government paramilitaries (like the Black and Tans or the miliciens). The violence may be secondary. Sometimes the resistance members are trying to capture equipment, documents, or intelligence; how many guerrillas have gotten started by killing occupying soldiers to get guns? Sometimes the attack is intended to force the enemy to increase its defensive garrisons or pull back to more defended positions and abandon remote or outlying areas. Sometimes the point is to demonstrate the strength or capabilities of the resistance to the population and the occupier. Sometimes the point is actually to kill enemy soldiers and deplete the occupying force. Sometimes the troops are just sentries or guards, and the primary target is an enemy building or facility.
Of course, for these attacks to happen successfully, they must follow the basic rules of asymmetric conflict and general good strategy. When raiding police stations for guns, the IRA chose remote, poorly guarded sites. Guerrillas like to go after locations with only one or two sentries, and any attack on those small sites forces the occupier to make tough choices: abandon an outpost because it can’t be adequately defended or increase security by doubling the number of guards. Either benefits the resistance and saps the resources of the occupier.
And although in industrial conflicts it’s often true that destroying materiel and disrupting logistics can be very effective, that’s sometimes not enough. Take American involvement in the Vietnam War. The American cost in terms of materiel was enormous—in modern dollars, the war cost close to $600 billion. But it wasn’t the cost of replacing helicopters or fueling convoys that turned US sentiment against the war. It was the growing stream of American bodies being flown home in coffins.
There’s a world of difference—socially, organizationally, psychologically—between fighting the occupation of a foreign government and the occupation of a domestic one. There’s something about the psychology of resistance that makes it easier for people to unite against a foreign enemy. Most people make no distinction between the people living in their country and the government of that country, which is why the news will say “America pulls out of climate talks” when they are talking about the US government. This psychology is why millions of Vietnamese people took up arms against the American invasion, but only a handful of Americans took up arms against that invasion (some of them being soldiers who fragged their officers, and some of them being groups like the Weather Underground who went out of their way not to injure the people who were burning Vietnamese peasants alive by the tens of thousands). This psychology explains why some of the patriots who fought in the French Resistance went on to torture people to repress the Algerian Resistance. And it explains why most Germans didn’t even support theoretical resistance against Hitler a decade after the war.
This doesn’t bode well for resistance in the minority world, where the rich and powerful minority live. People in poorer countries may be able to rally against foreign corporations and colonial dictatorships, but those in the center of empire contend with power structures that most people consider natural, familiar, even friendly. But these domestic institutions of power—be they corporate or governmental—are just as foreign, and just as destructive, as an invading army. They may be based in the same geographic region as we are, but they are just as alien as if they were run by robots or little green men.

Intimidation is another tactic related to violence that is usually conducted underground. This tactic is used by the “Gulabi Gang” (also called the Pink Sari Gang) of Uttar Pradesh, a state in India.4 Leader Sampat Pal Devi calls it “a gang for justice.” The Gulabi Gang formed as a response to deeply entrenched and violent patriarchy (especially domestic and sexual violence) and caste-based discrimination. The members use a variety of tactics to fight for women’s rights, but their “vigilante violence” has gained global attention. With over 500 members, they can exert considerable force. They’ve stopped child marriages. They’ve beaten up men who perpetrate domestic violence. The gang forced the police to register crimes against Untouchables by slapping police officers until they complied. They’ve hijacked trucks full of food that were going to be sold for a profit by corrupt officials. Their hundreds of members practice self-defense with the lathi (a traditional Indian stick or staff weapon). It’s no surprise their ranks are growing.

Gulabi Gang
Many of these examples tread the boundary of our aboveground-underground distinction. When struggling against systems of patriarchy that have closely allied themselves with governments and police (which is to say, virtually all systems of patriarchy), women’s groups that have been forced to use violence or the threat of violence may have to operate in a clandestine fashion at least some of the time. At the same time, the effects of their self-defense must be prominent and publicized. Killing a rapist or abuser has the obvious benefit of stopping any future abuses by that individual. But the larger beneficial effect is to intimidate other would-be abusers—to turn the tables and prevent other incidents of rape or abuse by making the consequences for perpetrators known. The Gulabi Gang is so popular and effective in part because they openly defy abuses of male power, so the effect on both men and women is very large. Their aboveground defiance rallies more support than they could by causing abusive men to die in a series of mysterious accidents. The Black Panthers were similarly popular because they publically defied the violent oppression meted out by police on a daily basis. And by openly bearing arms, they were able to intimidate the police (and other people, like drug dealers) into reducing their abuses.
There are limits to the use of intimidation on those in power. The most powerful people are the most physically isolated—they might have bodyguards or live in gated houses. They have far more coercive force at their fingertips than any resistance movement. For that reason, resistance groups have historically used intimidation primarily on low-level functionaries and collaborators who give information to those in power when asked or who cooperate with them in a more limited way.

No resistance movement wants to engage in needless cycles of violence and retribution with those in power. But a refusal to employ violent tactics when they are appropriate will very likely lead to more violence. Many abolitionists did not support John Brown because they considered his plan for a defensive liberation struggle to be too violent—but Brown’s failure led inevitably to a lengthy and gruesome Civil War (as well as continued years of bloody slavery), a consequence that was orders of magnitude more violent than Brown’s intended plan.

This leads us to the last major underground tactic: assassination.
In talking about assassination (or any attack on humans) in the context of resistance, two key questions must be asked. First, is the act strategically beneficial, that is, would assassination further the strategy of the group? Second, is the act morally just, given the person in question? (The issue of justice is necessarily particular to the target; it’s assumed that the broader strategy incorporates aims to increase justice.)
As is shown on my two-by-two grid of all combinations, an assassination may be strategic and just, it may be strategic and unjust, it may be unstrategic but just, or it may be both unstrategic and unjust. Obviously, any action in the last category would be out of the question. Any action in the strategic and just category could be a good bet for an armed resistance movement. The other two categories are where things get complex.
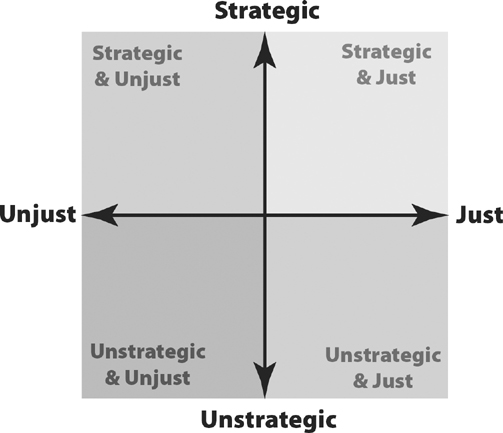
Figure 13-3
Once Hitler had risen to power in the late 1930s, though, his aim was clear, as he had already been whipping up hate and expanding his control of Nazi Germany. At that point, it would have been both strategic and just to assassinate him. Indeed, elements in the Wehrmacht (army) and the Abwehr (intelligence) considered it, because they knew what Hitler was planning to do. Unfortunately, they were indecisive, and did not commit to the plan. Hitler soon began invading Germany’s neighbors, and as his popularity soared, the assassination plan was shelved. It was years before inside elements would actually stage an assassination attempt.
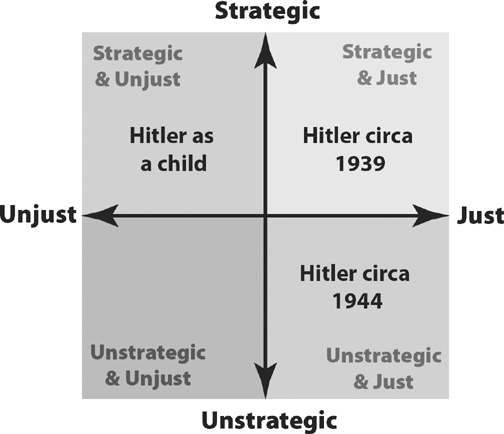
Figure 13-4
That famous attempt took place—and failed—on July 20, 1944.5What’s interesting is that the Allies were also considering an attempt on Hitler’s life, which they called Operation Foxley. They knew that Hitler routinely went on walks alone in a remote area, and devised a plan to parachute in two operatives dressed as German officers, one of them a sniper, who would lay in wait and assassinate Hitler when he walked by. The plan was never enacted because of internal controversy. Many in the SOE and British government believed that Hitler was a poor strategist, a maniac whose overreach would be his downfall. If he were assassinated, they believed, his replacement (likely Himmler) would be a more competent leader, and this would draw out the war and increase Allied losses. In the opinion of the Allies it was unquestionably just to kill Hitler, but no longer strategically beneficial.
There is no shortage of situations where assassination would have been just, but of questionable strategic value. Resistance groups pondering assassination have many questions to ask themselves in deciding whether they are being strategic or not. What is the value of this potential target to the enemy? Is this an exceptional person or does his or her influence come from his or her role in the organization? Who would replace this person, and would that person be better or worse for the struggle? Will it make any difference on an organizational scale or is the potential target simply an interchangeable cog? Uniquely valuable individuals make uniquely valuable targets for assassination by resistance groups.
Of course, in a military context (and this overlaps with attacks on troops), snipers routinely target officers over enlisted soldiers. In theory, officers or enlisted soldiers are standardized and replaceable, but, in practice, officers constitute more valuable targets. There’s a difference between theoretical and practical equivalence; there might be other officers to replace an assassinated one, but the replacement might not arrive in a timely manner nor would he have the experience of his predecessor (experience being a key reason that Michael Collins assassinated intelligence officers). That said, snipers don’t just target officers. Snipers target any enemy soldiers available, because war is essentially about destroying the other side’s ability to wage war.
The benefits must also outweigh costs or side effects. Resistance members may be captured or killed in the attempt. Assassination also provokes a major response—and major reprisals—because it is a direct attack on those in power. When SS boss Reinhard Heydrich (“the butcher of Prague”) was assassinated in 1942, the Nazis massacred more than 1,000 Czech people in response. In Canada, martial law (via the War Measures Act) has only ever been declared three times—during WWI and WWII, and again after the assassination of the Quebec Vice Premier of Quebec by the Front de Libération du Québec. Remember, aboveground allies may bear the brunt of reprisals for assassinations, and those reprisals can range from martial law and police crackdowns to mass arrests or even executions.
There’s an important distinction to be made between assassination as an ideological tactic versus as a military tactic. As a military tactic, employed by countless snipers in the history of war, assassination decisively weakens the adversary by killing people with important experience or talents, weakening the entire organization. Assassination as an ideological tactic—attacking or killing prominent figures because of ideological disagreements—almost always goes sour, and quickly. There are few more effective ways to create martyrs and trigger cycles of violence without actually accomplishing anything decisive. The assassination of Michael Collins, for example, by his former allies led only to bloody civil war.
DECISIVE OPERATIONS UNDERGROUND
Individuals working underground focus mostly on small-scale acts of sabotage and subversion that make the most of their skill and opportunity. Because they lack escape networks, and because they must be opportunistic, it’s ideal for their actions to be what French resisters called insaisissable–untraceable or appearing like an accident—unless the nature of the action requires otherwise.
Individual saboteurs are more effective with some informal coordination—if, for example, a general day of action has been called. It also helps if the individuals seize an opportunity by springing into action when those in power are already off balance or under attack, like the two teenaged French girls who sabotaged trains carrying German tanks after D-Day, thus hampering the German ability to respond to the Allied landing.
One individual resister who attempted truly decisive action was Georg Elser, a German-born carpenter who opposed Hitler from the beginning. When Hitler started the World War II in 1939, Elser resolved to assassinate Hitler. He spent hours every night secretly hollowing out a hidden cavity in the beer hall where Hitler spoke each year on the anniversary of his failed coup. Elser used knowledge he learned from working at a watch factory to build a timer, and planted a bomb in the hidden cavity. The bomb went off on time, but by chance Hilter left early and survived. When Elser was captured, the Gestapo tortured him for information, refusing to believe that a single tradesperson with a grade-school education could come so close to killing Hitler without help. But Elser, indeed, worked entirely alone.
Underground networks can accomplish decisive operations that require greater coordination, numbers, and geographic scope. This is crucial. Large-scale coordination can turn even minor tactics—like simple sabotage—into dramatically decisive events. Underground saboteurs from the French Resistance to the ANC relied on simple techniques, homemade tools, and “appropriate technology.” With synchronization between even a handful of groups, these underground networks can make an entire economy grind to a halt.
The change is more than quantitative, it’s qualitative. A massively coordinated set of actions is fundamentally different from an uncoordinated set of the same actions. Complex systems respond in a nonlinear fashion. They can adapt and maintain equilibrium in the face of small insults, minor disruptions. But beyond a certain point, increasing attacks undermine the entire system, causing widespread failure or collapse.
Because of this, coordination is perhaps the most compelling argument for underground networks over mere isolated cells. I’ll discuss coordinated actions in more detail in the next chapter: Decisive Ecological Warfare.
SUSTAINING OPERATIONS UNDERGROUND
Since individuals working underground are pretty much alone, they have very few options for sustaining operations. They may potentially recruit or train others to form an underground cell. Or they may try to make contact with other people or groups (either underground or aboveground) to work as an auxiliary of some kind, such as an intelligence source, especially if they are able to pass on information from inside a government or corporate bureaucracy. But making this connection is often very challenging.
Individual escape and evasion may also be a decisive or sustaining action, at least on a small scale. Antebellum American slavery offers some examples. In a discussion of slave revolts, historian Deborah Gray White explains, “[I]ndividual resistance did not overthrow slavery, but it might have encouraged masters to make perpetual servitude more tolerable and lasting. Still, for many African Americans, individual rebellions against the authority of slaveholders fulfilled much the same function as did the slave family, Christianity, and folk religion: it created the psychic space that enabled Black people to survive.”6
Historian John Michael Vlach observes: “Southern plantations actually served as the training grounds for those most inclined to seek their freedom.” Slaves would often escape for short periods of time as a temporary respite from compelled labor before returning to plantations, a practice often tolerated by owners. These escapes provided opportunities to build a camp or even steal and stock up on provisions for another escape. Sometimes slaves would use temporary escapes as attempts to compel better behavior from plantation owners.7 In any case, these escapes and minor thefts helped to build a culture of resistance by challenging the omnipotence of slave owners and reclaiming some small measure of autonomy and freedom.
Individuals have some ability to assert power, but recruitment is key in underground sustaining operations. A single cell can gather or steal equipment and supplies for itself, but it can’t participate in wider sustaining operations unless it forms a network by recruiting organizationally, training new members and auxiliaries, and extending into new cells. One underground cell is all you need to create an entire network. Creating the first cell—finding those first few trusted comrades, developing communications and signals—is the hardest part, because other cells can be founded on the same template, and the members of the existing cell can be used to recruit, screen, and train new members.
Even though it’s inherently difficult for an underground group to coordinate with other distinct underground groups, it is possible for an underground cell to offer supporting operations to aboveground campaigns. It was an underground group—the Citizen’s Commission to Investigate the FBI—that exposed COINTELPRO, and allowed many aboveground groups to understand and counteract the FBI’s covert attacks on them. And the judicious use of sabotage could buy valuable time for aboveground groups to mobilize in a given campaign.
There are clearly campaigns in which aboveground groups have no desire for help from the underground, in which case it’s best for the underground to focus on other projects. But the two can work together on the same strategy without direct coordination. If a popular aboveground campaign against a big-box store or unwanted new industrial site fails because of corrupt politicians, an underground group can always pick up the slack and damage or destroy the facility under construction. Sometimes people argue that there’s no point in sabotaging anything, because those in power will just build it again. But there may come a day when those in power start to say “there’s no point in building it—they’ll just burn it down again.”
Underground cells may also run a safehouse or safehouses for themselves and allies. Single cells can’t run true underground railroads, but even single safehouses are valuable in dealing with repression or persecution. A key challenge in underground railroads and escape lines is that the escapees have to make contact with underground helpers without exposing themselves to those in power. Larger, more “formalized” underground networks have specialized methods and personnel for this, but a single cell running a safehouse may not. If an underground cell is conscientious, its members will be the only ones aware that the safehouse exists at all, which puts the burden on them to contact someone who requires refuge.
Mass persecution and repression has happened enough times in history to provide a wealth of examples where this would be appropriate. The internment of Japanese Canadians during World War II is quite well-known. Less well-known is the internment of hundreds of leftist radicals and labor activists starting in 1940. Leading activists associated with certain other ethnic organizations (especially Ukrainian), the labor movement, and the Communist party were arrested and sent to isolated work camps in various locations around Canada. A few managed to go into hiding, at least temporarily, but the vast majority were captured and sent to the camps, where a number of them died.8 In a situation like that, an underground cell could offer shelter to a persecuted aboveground activist or activists on an invitational basis without having to expose themselves openly.
Many of these operations work in tandem. Resistance networks from the SOE to the ANC have used their escape lines and underground railroads to sneak recruits to training sites in friendly areas and then infiltrated those people back into occupied territory to take up the fight.
Underground networks may be large enough to create “areas of persistence” where they exert a sizeable influence and have developed an underground infrastructure rooted in a culture of resistance. If an underground network reaches a critical mass in a certain area, it may be able to significantly disrupt the command and control systems of those in power, allowing resisters both aboveground and underground a greater amount of latitude in their work.
There are a number of examples of resistance movements successfully creating areas of persistence. The Zapatistas in Mexico exert considerable influence in Chiapas, so much so that they can post signs to that effect. “You are in Zapatista rebel territory” proclaims one typical sign (translated from Spanish). “Here the people give the orders and the government obeys.” The posting also warns against drug and alcohol trafficking or use and against the illegal sale of wood. “No to the destruction of nature.”9 Other Latin American resistance movements, such as the FMLN in El Salvador and the Sandinistas in Nicaragua, created areas of persistence in Latin America in the late twentieth century. Hamas in Palestine and Hezbollah in Lebanon have similarly established large areas of persistence in the Middle East.
SHAPING OPERATIONS UNDERGROUND
Because working underground is dangerous and difficult, effective resisters mostly focus on decisive and sustaining operations that will be worth their while. That said, there are still some shaping operations for the underground.
This includes general counterintelligence and security work. Ferreting out and removing informers and infiltrators is a key step in allowing resistance organizations of every type to grow and resistance strategies to succeed. Neither the ANC nor the IRA were able to win until they could deal effectively with such people.
Underground cells can also carry out some specialized propaganda operations. For reasons already discussed, propaganda in general is best carried out by aboveground groups, but there are exceptions. In particularly repressive regimes, basic propaganda and education projects must move underground to continue to function and protect identities. Underground newspapers and forms of pirate radio are two examples. Entire, vast underground networks have been built on this principle. In Soviet Russia, samizdat was the secret copying of and distribution of illegal or censored texts. A person who received a piece of illegal literature—say, Vaclav Havel’s Power of the Powerless—was expected to make more copies and pass them on. In a pre–personal computer age, in a country where copy machines and printing presses were under state control, this often meant laboriously copying books by hand or typewriter.
Underground groups may also want to carry out certain high-profile or spectacular “demonstration” actions to demonstrate that underground resistance is possible and that it is happening, and to offer a model for a particular tactic or target to be emulated by others. Of course, demonstrative actions may be valuable, but they can also degrade into symbolism for the sake of symbolism. Plenty of underground groups, the Weather Underground included, hoped to use their actions to “ignite a revolution.” But, in general—and especially when “the masses” can’t be reasonably expected to join in the fight—underground groups must get their job done by being as decisive as possible.
Editor’s note: continue reading at Target Selection.









