by Deep Green Resistance News Service | Nov 11, 2018 | Strategy & Analysis
Featured image: power line sabotaged by the African National Congress
Editor’s note: The following is from the chapter “Tactics and Targets” of the book Deep Green Resistance: A Strategy to Save the Planet. This book is now available for free online.
by Aric McBay
Some tactics can be carried out underground—like general liberation organizing and propaganda—but are more effective aboveground. Where open speech is dangerous, these types of tactics may move underground to adapt to circumstances. The African National Congress, in its struggle for basic human rights, should have been allowed to work aboveground, but that simply wasn’t possible in repressive apartheid South Africa.
And then there are tactics that are only appropriate for the underground, obligate underground operations that depend on secrecy and security. Escape lines and safehouses for persecuted persons and resistance fugitives are example of those operations. There’s a reason it’s called the “underground” railroad—it’s not transferable to the aboveground, because the entire operation is completely dependent on secrecy. Clandestine intelligence gathering is another case; the French Resistance didn’t gather enemy secrets by walking up to the nearest SS office and asking for a list of their troop deployments.
Some tactics are almost always limited to the underground:
- Clandestine intelligence
- Escape
- Sabotage and attacks on materiel
- Attacks on troops
- Intimidation
- Assassination
As operational categories, intelligence and escape are pretty clear, and few people looking at historical struggles will deny the importance of gathering information or aiding people to escape persecution. Of course, some abolitionists in the antebellum US didn’t support the Underground Railroad. And many Jewish authorities tried to make German Jews cooperate with registration and population control measures. In hindsight, it’s clear to us that these were huge strategic and moral mistakes, but at the time it may only have been clear to the particularly perceptive and farsighted.
Sabotage and attacks on materiel are overlapping tactics. Oftentimes, sabotage is more subtle; for example, machinery may be disabled without being recognized as sabotage. Attacks on materiel are often more overt efforts to destroy and disable the adversary’s equipment and supplies. In any case, they form an inclusive continuum, with sabotage on the more clandestine end of the scale.
It’s true that harm can be caused through sabotage, and that sabotage can be a form of violence. But allowing a machine to operate can also be more violent than sabotaging it. Think of a drift net. How many living creatures does a drift net kill as it passes through the ocean, regardless of whether it’s being used for fishing or not? Destroying a drift net—or sabotaging a boat so that a drift net cannot be deployed—would save countless lives. Sabotaging a drift net is clearly a nonviolent act. However, you could argue conversely that not sabotaging a drift net (provided you had the means and opportunity) is a profoundly violent act—indeed, violent not just for individual creatures, but violent on a massive, ecological scale. The drift net is an obvious example, but we could make a similar (if longer and more roundabout) argument for most any industrial machinery.
You’re opposed to violence? So where’s your monkey wrench?
Sabotage is not categorically violent, but the next few underground categories may involve violence on the part of resisters. Attacks on troops, intimidation, assassination, and the like have been used to great effect by a great many resistance movements in history. From the assassination of SS officers by escaping concentration camp inmates to the killing of slave owners by revolting slaves to the assassination of British torturers by Michael Collins’s Twelve Apostles, the selective use of violence has been essential for victory in a great many resistance and liberation struggles.
Attacks on troops are common where a politically conscious population lives under overt military occupation. In these situations, there is often little distinction between uniformed militaries, police, and government paramilitaries (like the Black and Tans or the miliciens). The violence may be secondary. Sometimes the resistance members are trying to capture equipment, documents, or intelligence; how many guerrillas have gotten started by killing occupying soldiers to get guns? Sometimes the attack is intended to force the enemy to increase its defensive garrisons or pull back to more defended positions and abandon remote or outlying areas. Sometimes the point is to demonstrate the strength or capabilities of the resistance to the population and the occupier. Sometimes the point is actually to kill enemy soldiers and deplete the occupying force. Sometimes the troops are just sentries or guards, and the primary target is an enemy building or facility.
Of course, for these attacks to happen successfully, they must follow the basic rules of asymmetric conflict and general good strategy. When raiding police stations for guns, the IRA chose remote, poorly guarded sites. Guerrillas like to go after locations with only one or two sentries, and any attack on those small sites forces the occupier to make tough choices: abandon an outpost because it can’t be adequately defended or increase security by doubling the number of guards. Either benefits the resistance and saps the resources of the occupier.
And although in industrial conflicts it’s often true that destroying materiel and disrupting logistics can be very effective, that’s sometimes not enough. Take American involvement in the Vietnam War. The American cost in terms of materiel was enormous—in modern dollars, the war cost close to $600 billion. But it wasn’t the cost of replacing helicopters or fueling convoys that turned US sentiment against the war. It was the growing stream of American bodies being flown home in coffins.
There’s a world of difference—socially, organizationally, psychologically—between fighting the occupation of a foreign government and the occupation of a domestic one. There’s something about the psychology of resistance that makes it easier for people to unite against a foreign enemy. Most people make no distinction between the people living in their country and the government of that country, which is why the news will say “America pulls out of climate talks” when they are talking about the US government. This psychology is why millions of Vietnamese people took up arms against the American invasion, but only a handful of Americans took up arms against that invasion (some of them being soldiers who fragged their officers, and some of them being groups like the Weather Underground who went out of their way not to injure the people who were burning Vietnamese peasants alive by the tens of thousands). This psychology explains why some of the patriots who fought in the French Resistance went on to torture people to repress the Algerian Resistance. And it explains why most Germans didn’t even support theoretical resistance against Hitler a decade after the war.
This doesn’t bode well for resistance in the minority world, where the rich and powerful minority live. People in poorer countries may be able to rally against foreign corporations and colonial dictatorships, but those in the center of empire contend with power structures that most people consider natural, familiar, even friendly. But these domestic institutions of power—be they corporate or governmental—are just as foreign, and just as destructive, as an invading army. They may be based in the same geographic region as we are, but they are just as alien as if they were run by robots or little green men.

Intimidation is another tactic related to violence that is usually conducted underground. This tactic is used by the “Gulabi Gang” (also called the Pink Sari Gang) of Uttar Pradesh, a state in India.4 Leader Sampat Pal Devi calls it “a gang for justice.” The Gulabi Gang formed as a response to deeply entrenched and violent patriarchy (especially domestic and sexual violence) and caste-based discrimination. The members use a variety of tactics to fight for women’s rights, but their “vigilante violence” has gained global attention. With over 500 members, they can exert considerable force. They’ve stopped child marriages. They’ve beaten up men who perpetrate domestic violence. The gang forced the police to register crimes against Untouchables by slapping police officers until they complied. They’ve hijacked trucks full of food that were going to be sold for a profit by corrupt officials. Their hundreds of members practice self-defense with the lathi (a traditional Indian stick or staff weapon). It’s no surprise their ranks are growing.

Gulabi Gang
Many of these examples tread the boundary of our aboveground-underground distinction. When struggling against systems of patriarchy that have closely allied themselves with governments and police (which is to say, virtually all systems of patriarchy), women’s groups that have been forced to use violence or the threat of violence may have to operate in a clandestine fashion at least some of the time. At the same time, the effects of their self-defense must be prominent and publicized. Killing a rapist or abuser has the obvious benefit of stopping any future abuses by that individual. But the larger beneficial effect is to intimidate other would-be abusers—to turn the tables and prevent other incidents of rape or abuse by making the consequences for perpetrators known. The Gulabi Gang is so popular and effective in part because they openly defy abuses of male power, so the effect on both men and women is very large. Their aboveground defiance rallies more support than they could by causing abusive men to die in a series of mysterious accidents. The Black Panthers were similarly popular because they publically defied the violent oppression meted out by police on a daily basis. And by openly bearing arms, they were able to intimidate the police (and other people, like drug dealers) into reducing their abuses.
There are limits to the use of intimidation on those in power. The most powerful people are the most physically isolated—they might have bodyguards or live in gated houses. They have far more coercive force at their fingertips than any resistance movement. For that reason, resistance groups have historically used intimidation primarily on low-level functionaries and collaborators who give information to those in power when asked or who cooperate with them in a more limited way.

No resistance movement wants to engage in needless cycles of violence and retribution with those in power. But a refusal to employ violent tactics when they are appropriate will very likely lead to more violence. Many abolitionists did not support John Brown because they considered his plan for a defensive liberation struggle to be too violent—but Brown’s failure led inevitably to a lengthy and gruesome Civil War (as well as continued years of bloody slavery), a consequence that was orders of magnitude more violent than Brown’s intended plan.

This leads us to the last major underground tactic: assassination.
In talking about assassination (or any attack on humans) in the context of resistance, two key questions must be asked. First, is the act strategically beneficial, that is, would assassination further the strategy of the group? Second, is the act morally just, given the person in question? (The issue of justice is necessarily particular to the target; it’s assumed that the broader strategy incorporates aims to increase justice.)
As is shown on my two-by-two grid of all combinations, an assassination may be strategic and just, it may be strategic and unjust, it may be unstrategic but just, or it may be both unstrategic and unjust. Obviously, any action in the last category would be out of the question. Any action in the strategic and just category could be a good bet for an armed resistance movement. The other two categories are where things get complex.
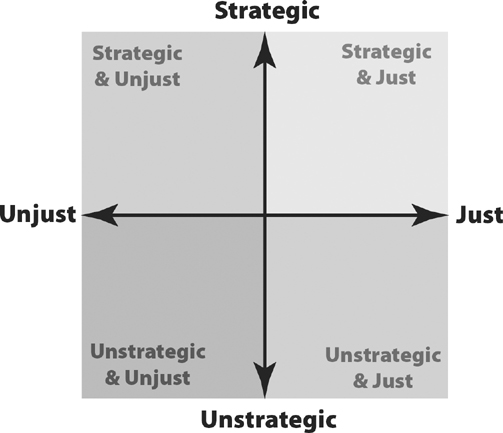
Figure 13-3
Once Hitler had risen to power in the late 1930s, though, his aim was clear, as he had already been whipping up hate and expanding his control of Nazi Germany. At that point, it would have been both strategic and just to assassinate him. Indeed, elements in the Wehrmacht (army) and the Abwehr (intelligence) considered it, because they knew what Hitler was planning to do. Unfortunately, they were indecisive, and did not commit to the plan. Hitler soon began invading Germany’s neighbors, and as his popularity soared, the assassination plan was shelved. It was years before inside elements would actually stage an assassination attempt.
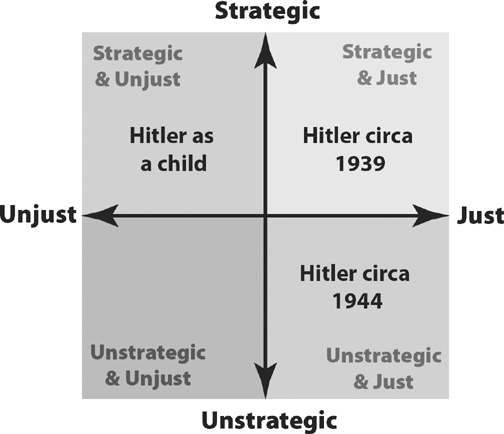
Figure 13-4
That famous attempt took place—and failed—on July 20, 1944.5What’s interesting is that the Allies were also considering an attempt on Hitler’s life, which they called Operation Foxley. They knew that Hitler routinely went on walks alone in a remote area, and devised a plan to parachute in two operatives dressed as German officers, one of them a sniper, who would lay in wait and assassinate Hitler when he walked by. The plan was never enacted because of internal controversy. Many in the SOE and British government believed that Hitler was a poor strategist, a maniac whose overreach would be his downfall. If he were assassinated, they believed, his replacement (likely Himmler) would be a more competent leader, and this would draw out the war and increase Allied losses. In the opinion of the Allies it was unquestionably just to kill Hitler, but no longer strategically beneficial.
There is no shortage of situations where assassination would have been just, but of questionable strategic value. Resistance groups pondering assassination have many questions to ask themselves in deciding whether they are being strategic or not. What is the value of this potential target to the enemy? Is this an exceptional person or does his or her influence come from his or her role in the organization? Who would replace this person, and would that person be better or worse for the struggle? Will it make any difference on an organizational scale or is the potential target simply an interchangeable cog? Uniquely valuable individuals make uniquely valuable targets for assassination by resistance groups.
Of course, in a military context (and this overlaps with attacks on troops), snipers routinely target officers over enlisted soldiers. In theory, officers or enlisted soldiers are standardized and replaceable, but, in practice, officers constitute more valuable targets. There’s a difference between theoretical and practical equivalence; there might be other officers to replace an assassinated one, but the replacement might not arrive in a timely manner nor would he have the experience of his predecessor (experience being a key reason that Michael Collins assassinated intelligence officers). That said, snipers don’t just target officers. Snipers target any enemy soldiers available, because war is essentially about destroying the other side’s ability to wage war.
The benefits must also outweigh costs or side effects. Resistance members may be captured or killed in the attempt. Assassination also provokes a major response—and major reprisals—because it is a direct attack on those in power. When SS boss Reinhard Heydrich (“the butcher of Prague”) was assassinated in 1942, the Nazis massacred more than 1,000 Czech people in response. In Canada, martial law (via the War Measures Act) has only ever been declared three times—during WWI and WWII, and again after the assassination of the Quebec Vice Premier of Quebec by the Front de Libération du Québec. Remember, aboveground allies may bear the brunt of reprisals for assassinations, and those reprisals can range from martial law and police crackdowns to mass arrests or even executions.
There’s an important distinction to be made between assassination as an ideological tactic versus as a military tactic. As a military tactic, employed by countless snipers in the history of war, assassination decisively weakens the adversary by killing people with important experience or talents, weakening the entire organization. Assassination as an ideological tactic—attacking or killing prominent figures because of ideological disagreements—almost always goes sour, and quickly. There are few more effective ways to create martyrs and trigger cycles of violence without actually accomplishing anything decisive. The assassination of Michael Collins, for example, by his former allies led only to bloody civil war.
DECISIVE OPERATIONS UNDERGROUND
Individuals working underground focus mostly on small-scale acts of sabotage and subversion that make the most of their skill and opportunity. Because they lack escape networks, and because they must be opportunistic, it’s ideal for their actions to be what French resisters called insaisissable–untraceable or appearing like an accident—unless the nature of the action requires otherwise.
Individual saboteurs are more effective with some informal coordination—if, for example, a general day of action has been called. It also helps if the individuals seize an opportunity by springing into action when those in power are already off balance or under attack, like the two teenaged French girls who sabotaged trains carrying German tanks after D-Day, thus hampering the German ability to respond to the Allied landing.
One individual resister who attempted truly decisive action was Georg Elser, a German-born carpenter who opposed Hitler from the beginning. When Hitler started the World War II in 1939, Elser resolved to assassinate Hitler. He spent hours every night secretly hollowing out a hidden cavity in the beer hall where Hitler spoke each year on the anniversary of his failed coup. Elser used knowledge he learned from working at a watch factory to build a timer, and planted a bomb in the hidden cavity. The bomb went off on time, but by chance Hilter left early and survived. When Elser was captured, the Gestapo tortured him for information, refusing to believe that a single tradesperson with a grade-school education could come so close to killing Hitler without help. But Elser, indeed, worked entirely alone.
Underground networks can accomplish decisive operations that require greater coordination, numbers, and geographic scope. This is crucial. Large-scale coordination can turn even minor tactics—like simple sabotage—into dramatically decisive events. Underground saboteurs from the French Resistance to the ANC relied on simple techniques, homemade tools, and “appropriate technology.” With synchronization between even a handful of groups, these underground networks can make an entire economy grind to a halt.
The change is more than quantitative, it’s qualitative. A massively coordinated set of actions is fundamentally different from an uncoordinated set of the same actions. Complex systems respond in a nonlinear fashion. They can adapt and maintain equilibrium in the face of small insults, minor disruptions. But beyond a certain point, increasing attacks undermine the entire system, causing widespread failure or collapse.
Because of this, coordination is perhaps the most compelling argument for underground networks over mere isolated cells. I’ll discuss coordinated actions in more detail in the next chapter: Decisive Ecological Warfare.
SUSTAINING OPERATIONS UNDERGROUND
Since individuals working underground are pretty much alone, they have very few options for sustaining operations. They may potentially recruit or train others to form an underground cell. Or they may try to make contact with other people or groups (either underground or aboveground) to work as an auxiliary of some kind, such as an intelligence source, especially if they are able to pass on information from inside a government or corporate bureaucracy. But making this connection is often very challenging.
Individual escape and evasion may also be a decisive or sustaining action, at least on a small scale. Antebellum American slavery offers some examples. In a discussion of slave revolts, historian Deborah Gray White explains, “[I]ndividual resistance did not overthrow slavery, but it might have encouraged masters to make perpetual servitude more tolerable and lasting. Still, for many African Americans, individual rebellions against the authority of slaveholders fulfilled much the same function as did the slave family, Christianity, and folk religion: it created the psychic space that enabled Black people to survive.”6
Historian John Michael Vlach observes: “Southern plantations actually served as the training grounds for those most inclined to seek their freedom.” Slaves would often escape for short periods of time as a temporary respite from compelled labor before returning to plantations, a practice often tolerated by owners. These escapes provided opportunities to build a camp or even steal and stock up on provisions for another escape. Sometimes slaves would use temporary escapes as attempts to compel better behavior from plantation owners.7 In any case, these escapes and minor thefts helped to build a culture of resistance by challenging the omnipotence of slave owners and reclaiming some small measure of autonomy and freedom.
Individuals have some ability to assert power, but recruitment is key in underground sustaining operations. A single cell can gather or steal equipment and supplies for itself, but it can’t participate in wider sustaining operations unless it forms a network by recruiting organizationally, training new members and auxiliaries, and extending into new cells. One underground cell is all you need to create an entire network. Creating the first cell—finding those first few trusted comrades, developing communications and signals—is the hardest part, because other cells can be founded on the same template, and the members of the existing cell can be used to recruit, screen, and train new members.
Even though it’s inherently difficult for an underground group to coordinate with other distinct underground groups, it is possible for an underground cell to offer supporting operations to aboveground campaigns. It was an underground group—the Citizen’s Commission to Investigate the FBI—that exposed COINTELPRO, and allowed many aboveground groups to understand and counteract the FBI’s covert attacks on them. And the judicious use of sabotage could buy valuable time for aboveground groups to mobilize in a given campaign.
There are clearly campaigns in which aboveground groups have no desire for help from the underground, in which case it’s best for the underground to focus on other projects. But the two can work together on the same strategy without direct coordination. If a popular aboveground campaign against a big-box store or unwanted new industrial site fails because of corrupt politicians, an underground group can always pick up the slack and damage or destroy the facility under construction. Sometimes people argue that there’s no point in sabotaging anything, because those in power will just build it again. But there may come a day when those in power start to say “there’s no point in building it—they’ll just burn it down again.”
Underground cells may also run a safehouse or safehouses for themselves and allies. Single cells can’t run true underground railroads, but even single safehouses are valuable in dealing with repression or persecution. A key challenge in underground railroads and escape lines is that the escapees have to make contact with underground helpers without exposing themselves to those in power. Larger, more “formalized” underground networks have specialized methods and personnel for this, but a single cell running a safehouse may not. If an underground cell is conscientious, its members will be the only ones aware that the safehouse exists at all, which puts the burden on them to contact someone who requires refuge.
Mass persecution and repression has happened enough times in history to provide a wealth of examples where this would be appropriate. The internment of Japanese Canadians during World War II is quite well-known. Less well-known is the internment of hundreds of leftist radicals and labor activists starting in 1940. Leading activists associated with certain other ethnic organizations (especially Ukrainian), the labor movement, and the Communist party were arrested and sent to isolated work camps in various locations around Canada. A few managed to go into hiding, at least temporarily, but the vast majority were captured and sent to the camps, where a number of them died.8 In a situation like that, an underground cell could offer shelter to a persecuted aboveground activist or activists on an invitational basis without having to expose themselves openly.
Many of these operations work in tandem. Resistance networks from the SOE to the ANC have used their escape lines and underground railroads to sneak recruits to training sites in friendly areas and then infiltrated those people back into occupied territory to take up the fight.
Underground networks may be large enough to create “areas of persistence” where they exert a sizeable influence and have developed an underground infrastructure rooted in a culture of resistance. If an underground network reaches a critical mass in a certain area, it may be able to significantly disrupt the command and control systems of those in power, allowing resisters both aboveground and underground a greater amount of latitude in their work.
There are a number of examples of resistance movements successfully creating areas of persistence. The Zapatistas in Mexico exert considerable influence in Chiapas, so much so that they can post signs to that effect. “You are in Zapatista rebel territory” proclaims one typical sign (translated from Spanish). “Here the people give the orders and the government obeys.” The posting also warns against drug and alcohol trafficking or use and against the illegal sale of wood. “No to the destruction of nature.”9 Other Latin American resistance movements, such as the FMLN in El Salvador and the Sandinistas in Nicaragua, created areas of persistence in Latin America in the late twentieth century. Hamas in Palestine and Hezbollah in Lebanon have similarly established large areas of persistence in the Middle East.
SHAPING OPERATIONS UNDERGROUND
Because working underground is dangerous and difficult, effective resisters mostly focus on decisive and sustaining operations that will be worth their while. That said, there are still some shaping operations for the underground.
This includes general counterintelligence and security work. Ferreting out and removing informers and infiltrators is a key step in allowing resistance organizations of every type to grow and resistance strategies to succeed. Neither the ANC nor the IRA were able to win until they could deal effectively with such people.
Underground cells can also carry out some specialized propaganda operations. For reasons already discussed, propaganda in general is best carried out by aboveground groups, but there are exceptions. In particularly repressive regimes, basic propaganda and education projects must move underground to continue to function and protect identities. Underground newspapers and forms of pirate radio are two examples. Entire, vast underground networks have been built on this principle. In Soviet Russia, samizdat was the secret copying of and distribution of illegal or censored texts. A person who received a piece of illegal literature—say, Vaclav Havel’s Power of the Powerless—was expected to make more copies and pass them on. In a pre–personal computer age, in a country where copy machines and printing presses were under state control, this often meant laboriously copying books by hand or typewriter.
Underground groups may also want to carry out certain high-profile or spectacular “demonstration” actions to demonstrate that underground resistance is possible and that it is happening, and to offer a model for a particular tactic or target to be emulated by others. Of course, demonstrative actions may be valuable, but they can also degrade into symbolism for the sake of symbolism. Plenty of underground groups, the Weather Underground included, hoped to use their actions to “ignite a revolution.” But, in general—and especially when “the masses” can’t be reasonably expected to join in the fight—underground groups must get their job done by being as decisive as possible.
Editor’s note: continue reading at Target Selection.

by Deep Green Resistance News Service | Aug 16, 2018 | Repression at Home
THE CIA, NSA, FBI AND DOD ARE YOUR “FRIENDS” ON FACEBOOK
by Lauren Smith / Wrong Kind of Green
Social media and Google serve three strategic purposes for the United States government. First, they allow Washington to conduct espionage; second, they facilitate the spread of disinformation campaigns, and third, they serve as conduits for the transmission of social contagions. In deploying thought control against the users of social media and Google, the US government regulates civil unrest both domestic and abroad. As such, social media and Google can best be understood as unconventional weapons (UW). In this capacity, they can be used in proxy wars against the governments of non-compliant Non-Aligned Movement (NAM) nations to accomplish regime change.
Through geopolitical manipulations that eliminate opposition, the United States government can actualize the ruling elites’ vision of a corporate controlled global economy without the deployment of troops. This model of “non-violence” or “soft-coup” as a method of unconventional warfare can be traced to Gene Sharp and the Albert Einstein Institution. It is organized through the efforts of the NGOs it oversees such as Freedom House and the National Endowment for Democracy (NED). And, it can be observed in the various Color Revolutions that occurred in Eastern European countries, the Middle East and now Latin America.
The NED is the coordinating Washington agency for regime destabilization and change. It is active from Tibet to Ukraine, from Venezuela to Tunisia, from Kuwait to Morocco in reshaping the world after the collapse of the Soviet Union into what George H.W. Bush in a 1991 speech to Congress proclaimed triumphantly as the dawn of a New World Order.”
Within this context, activists and the NAM must consider Facebook, Twitter, YouTube and Google hostile territory that is ultimately controlled by the United States Intelligence Community (IC) and the Department of Defense (DoD). Despite user-friendly packaging and attractive advertisements, social media and Google remain militarized programs. As such, activists and NAM users must enter with caution, prepared to do battle to win at PSYOPS in cyber warfare.
Using the US DoD model, cyber warfare can be upgraded to a department on par with the NAM armed forces. In this regard, Polytechnic universities are strategic and can be controlled by NAM governments and their operatives, as they are in the US by the IC and DoD. NAM military institutions can recruit cyber warfare teachers/activists, develop educational curriculum, set career paths and train cyber soldiers to counter US engagements. Useful information can be taken directly from any of the US military’s cyberspace recruitment sites, which promise to develop capabilities to defend national security as well as to create effects in cyberspace to achieve national objectives.
The first step for the NAM is to create public awareness of the threat that social media possesses to protect users and the NAM governments against its influence. In doing so, a cadre of civilian cyber PSYOP content monitors can be created. Additionally, software is now commercially available that can search, monitor, analyze and manage social media content. Presently, large corporations as well at the IC and DoD are using this social media software – since it is useful in business marketing strategies. NAM governments can deploy this software in their communication offices. Through vigilance, PSYOP efforts against NAM governments by social media and Google can be thwarted.
Concurrently, it is critical to guard against cyber invasion through the passing of cyber laws with strong penalties, as done by Germany with its groundbreaking Network Enforcement Act (NetzDG). Also, it is key to ensure through news media communications that workers in the IT industry understand the ramifications of the work in which they engage as well the nefarious intent of their respective employers. The “Never Again Pledge” taken by US tech workers in 2017 is promising.
Germany’s Network Enforcement Act (NetzDG)
Germany has blazed a trail for the NAM against PSYOPS in social media with its Network Enforcement Act (NetzDG) and it’s setting of finesof up to $50 million euros.ii The NAM must immediately follow suit with the setting of robust laws and fines against: the dissemination of propaganda; the encouragement of violent offences endangering the state; treasonous forgery; public incitement to crime; breaching of the public peace by threatening to commit offences; the forming of criminal or terrorist organizations.
Never Again Pledge
As reported by the New Yorker in its March 14, 2017 article titled: Why Protesters Gathered Outside Peter Thiel’s Mansion This Weekend, a group of about fifty tech workers, attorneys and anti-surveillance activists stood outside the home of Peter Thiel. Thiel is co-founded of Palantir Technologies, a Trump advisor, and was Facebook’s first investor. He remains a board member of Facebook as well as a member of the Bilderberg Steering Committee. The protest was organized to bring attention to software developed by Plantir called Investigative Case Management that is used by Immigration and Customs Enforcement (ICE) for mass deportation. Amongst other data sources to identify and track a given target, it uses social media content.
Since the presidential election, nearly three thousand tech workers signed the Never Again Pledge, promising to not work on databases that the Trump Administration might use to target vulnerable groups. The name is a nod to I.B.M.’s alleged role, during the Second World War, in systematizing Nazi genocide by providing punch-card technology.
“The banality of evil today is the person sitting in a cubicle in San Francisco, or in Silicon Valley, building the tools of digital fascism that are being used by those in Washington,”
To understand the US governments offensive against unfavorable NAM regimes, it is important to understand two things: first, the origin of Facebook and Google; and second, the influence they collectively wield over human motivation through coercion and the spread of social contagions through distorted reality. Within this context, it is of primary concern that activists become adept at the stealth guerilla tactic of hit-and-run, as flexibility and anonymity become key to survival. With the stakes of financial ruin, imprisonment and death so high under the USA Patriot Act, no dissident remains safe.
USA Patriot Act
As dissent and protest both international and domestic becomes increasingly illegal in the United States, and the governmental powers to investigate “terrorism” expand and morph under the USA Patriot Act, activists and the NAM must develop and foster skill sets that protect sympathetic Internet hosts, contributors and content against attack wherever they reside. According to the American Civil Liberties Union (ACLU), the Patriot Act increases the government’s surveillance powers in four areas:
-
Records searches. It expands the government’s ability to look at records on an individual’s activity being held by a third party. (Section 215)
-
Secret searches. It expands the government’s ability to search private property without notice to the owner. (Section 213)
-
Intelligence searches. It expands a narrow exception to the Fourth Amendment that had been created for the collection of foreign intelligence information (Section 218).
-
“Trap and trace” searches. It expands another Fourth Amendment exception for spying that collects “addressing” information about the origin and destination of communications, as opposed to the content (Section 214).
Accordingly, as described by the ACLU:
-
The government no longer has to show evidence that the subjects of search orders are an “agent of a foreign power,” a requirement that previously protected Americans against abuse of this authority.
-
The FBI does not even have to show a reasonable suspicion that the records are related to criminal activity, much less the requirement for “probable cause” that is listed in the Fourth Amendment to the Constitution. All the government needs to do is make the broad assertion that the request is related to an ongoing terrorism or foreign intelligence investigation.
-
Judicial oversight of these new powers is essentially non-existent. The government must only certify to a judge – with no need for evidence or proof – that such a search meets the statute’s broad criteria, and the judge does not even have the authority to reject the application.
-
Surveillance orders can be based in part on a person’s First Amendment activities, such as the books they read, the Web sites they visit, or a letter to the editor they have written.
-
A person or organization forced to turn over records is prohibited from disclosing the search to anyone. As a result of this gag order, the subjects of surveillance never even find out that their personal records have been examined by the government. That undercuts an important check and balance on this power: the ability of individuals to challenge illegitimate searches.
The ACLU also describes non-surveillance provisions in the Act, which remain the most serious as they enable the indefinite detention of non-citizens without trial. The provisions:
-
Give the Director of Central Intelligence the power to identify domestic intelligence requirements. As the director is appointed by the president, this extraordinary unchecked executive power opens the door to the same abuses that took place in the 1970s and before, when the CIA engaged in widespread spying on protest groups and other Americans.
-
Create a new crime of “domestic terrorism.” The Patriot Act transforms protesters into terrorists if they engage in conduct that “involves acts dangerous to human life” to “influence the policy of a government by intimidation or coercion.” The words “influence” and “coercion” have a wide range of meanings and allow for unbridled discretion. Furthermore, the law gives the attorney general and the secretary of state the power to detain or deport any non-citizen who belongs to or donates money to a broadly defined “domestic terrorist” group.
-
Allow for the indefinite detention of non-citizens. The attorney general can order detention based on a certification that he or she has “reasonable grounds to believe” a non-citizen endangers national security. Tangible proof is not a requirement, only a “reasonable belief”. Worse yet, if the foreigner does not have a country that will accept them, they can be detained indefinitely without trial.
US News Media: Counterpunch, Alice Donovan & the FBI
On December 25, 2017, a troubling article appeared in Counterpunch, a US media news outlet, regarding the writing of an alleged journalist/Russian troll, Alice Donovan. Links to an additional article appeared on Counterpunch’s Facebook page on July 27, 2018. Overall, the articles allege Donavan is either an unimaginative writer that committed plagiarism as a sport, or that she is a Russian troll. However, Donovan’s transgressions and intent are irrevelant, what the story revealed in all its gory horror is how the US government concocts justifications to learn the identity and location of a given dissident, and how easily it scared an independent and alternative US news media outlet into become its slobbering accomplice.
In this case, the FBI alleged Donovan was a Russian agent that spread disinformation in the Clinton/Trump presidential campaign with the intent of effecting the national election, despite the fact that she did not submit articles specifically on Clinton or Trump. What the US government’s fishing expedition also revealed is that all US news media can’t be trusted, even ones with cute sounding reactionary names, such as Counterpunch. As Counterpunch not only admitted to bending over backwards to cooperate with the FBI, it also proudly declared its decision to up-the-ante and conduct its own investigation and exposé. Counterpunch analyzed the transmission times and IP address of Donovan’s submission emails; it included photos of the alleged Alice Donovan from other media sources in its articles about her; it interviewed other news media that hosted Donovan’s articles, and most outrageously actually asked Donovan to call them by phone and send a photo of her utility bill disclosing her physical location. Without surprise, Donovan declined both requests stating: “security reasons.” If there was ever a reason to give up US hosted media, write under a nom de plume, use a Virtual Private Network (VPN), and accept payment only in crypto currency, this is it!
As anyone honestly committed to telling the truth will explain, it’s not about the messenger; it’s about the message. Under the Patriot Act, writers are safer in anonymity. But as anyone committed to telling the truth will also explain, when you eliminate one activist, ten are energized to take their respective place. Contrary to what PSYOPS wants the 99 percent to believe, there is strength in numbers. While imperialist greed through big payoffs may make for fast friendships, the shared love of truth and justice is priceless. It engenders a loyalty so strong it overcomes setbacks and hardship.
Origin of Facebook & Google
While the development of the Internet, data collection, surveillance and the global positioning system (GPS) can be attributed to the Department of Defense (DoD), Facebook and Google are also inexplicably linked to the CIA’s non-profit venture capital corporation, In-Q-Tel (IQT).
Within this context, Facebook can best be understood as the “friendly” replacement of DoD’s unpopular Information Awareness Office (IAO) which was created by its Defense Advanced Research Projects Agency (DARPA) in 2002 and defunded shortly thereafter in February 2003 by congress, due to public criticism that the development and deployment of its technology could potentially lead to an Orwellian styled mass surveillance system. The timing of Facebook’s development from the standpoint of DoD can at minimum be understood in regard to continuity as fortuitous if not planned – since Zuckerberg is credited with having launched Facebook on February 4, 2004 (within one year of IAO’s defunding).
Information Awareness Office (IAO) the Precursor to Facebook
As the precursor to Facebook, the Information Awareness Office (IAO) brought together several DARPA projects focused on applying surveillance with information technology by creating enormous computer databases to gather and store the personal information of everyone in the United States, including personal e-mails, social networks, credit card records, phone calls, medical records, and numerous other sources, without any requirement for a search warrant.
This information was then analyzed to look for suspicious activities, connections between individuals, and threats with the goal to increase the probability that authorized agencies of the United States could preempt adverse actions. It is important to note that adverse actions within this context are nebulous and thereby include any action that is perceived to counter US corporate short-term interests and security. Adverse actions as defined can include protests on both international and domestic issues by groups or individuals in thought, word or deed. Thus, internationally, those seeking to defend NAM countries against destabilization, invasion and occupation are engaged in adverse actions; and domestically, those seeking to protect human rights, constitutional rights and the environment are involved in adverse actions.
Just like IAO, Facebook invades and collects the email and telephone numbers of its users’ contacts in its Messenger component. Additionally, Facebook logs all photos and communications. Through its facial recognition component, Facebook links physical identities with names, locations, dates and times for easy surveillance. It also has a payment option, which allows Facebook to gain access to the financial institutions of its users. Groups centered on medical topics are densely populated on Facebook, and they encourage users to share their medical issues upon joining.
Facebook encourages its users to “complete their online profile” and list highly personal information such as: birthdate, gender, family members, school, workplace, intimate relationship, interests, religious and political views, hometown, current city as well as group affiliations. Through the recording of “likes” a granular sense of its users’ values and interests is also made known. This information, when taken in aggregate, allows for a profile so detailed and comprehensive that it amounts to a DoD agent’s wet dream.
According to Dave Chaffey in the Global Social Media Research summary, the number of social media users worldwide in 2018 is3.196 billion. Statista claims Facebook has 2.2 billion active monthly user accounts; YouTube has 1.9 billion; Instagram has 1 billion; and Twitter has 336 thousand. Within this context, social media’s sphere of influence is enormous, as the earth’s population is estimated to be 7.6 billion in 2018, according to Worldometers.
Cutting Edge Social Media Metadata Scanning, Analysis and Management Software
Realizing anything written on this topic is already expired and anything truly mind-bending is classified and beyond reach, there is still a nifty development worth mentioning regarding social media data scanning, analysis and management software. Clearly NAM can benefit by utilizing social media software of this ilk to transmit communications to constituents, gauge reactions to proposed initiatives, and most importantly in the context of this article, quickly identify and stave off destabilizing social media surprise attacks by imperialist powers and their agents. This technology can be considered a 2018 anti ballistic missile (ABM) to social media attacks.
According to Wired media, in its 2009 article titled U.S. Spies Buy Stake in Firm that Monitors Blogs & Tweets, the CIA’s venture capital nonprofit, IQT wanted Visible Technologies, a software firm that specializes in monitoring social media, to keep track of foreign social media, and provide early-warning detection on how issues are playing internationally. With this technology it is also possible for intelligence agencies to compile information on political figures, critics, journalists or others, and to exploit such information for political advantage. Visible’s foreign languages capabilities include Arabic, French, Spanish and nine other languages.
According to G2 Crowd, a Software & Services marketing firm, the latest 2018 must-have in business software is a Social Media Suite. The suite has the capability to manage, monitor, and analyze information related to one or multiple social media accounts through a single product. As such, it can:
-
Plan and publish digital content via social media
-
Engage with communities via social media
-
Report on effectiveness of social media practices
-
Track regions and demographics of audience
-
Analyze performance of posts and campaigns
-
Monitor for related mentions and trends
Facebook and the Cambridge Analytica Scandal
Through third parties, Facebook, alike its forerunner IAO, permitted the analysis of its users data. In the Cambridge Analytica (CA) scandal it was revealed that Facebook exposed the personal data of 87 million users to a political consulting firm in which Trump advisor, Steve Bannon, was its vice president and founder. The intent was to use personal data against users to influence their respective vote in the 2016 US presidential election in favor of Trump. The work of CA was done by the SCL Group, its parent company. SCL describes its capabilities as Vox’s Andrew Prokop writes:
“SCL tends to describe its capabilities in grandiose and somewhat unsettling language – the company has touted its expertise at ”psychological warfare” and “influence operations.” It’s long claimed that its sophisticated understanding of human psychology helps it target and persuade people of its clients’ preferred message.”
It is important to note that SCL’s main client is NATO and the defense department of its member states. Another company that was involved in this scandal is Palantir. Peter Thiel, is Palantir’s chairman and founder, as well as a major contributor in the Trump campaign. Palantir not only has numerous contracts with the US Intelligence Community and Department of Defense like the SCL Group, but Thiel was Facebook’s primary investor, and he remains on its board of directors.
CA whistleblower Chris Wylie told British Members of Parliament that senior Palantir employees worked with the firm on the Facebook data to help it build models off of the dataset to use for political ad targeting purposes.
Facebook’s Social Contagion Study Scandal
Another known scandal involving Facebook is the Social Contagion Study, which was undertaken in 2012 by researchers from Facebook, Cornell University, and the University of California.
In the study, the posts of approximately 700,000 unsuspecting users of Facebook were secretly manipulated, for a week, to determine how emotional states were transmitted over the platform. In the experiment, Facebook altered the news feed content of users to control the number of posts that contained words with positive or negative charged emotions to spy on the users’ reactions. They found negative feeds resulted in the user making negative posts, where as positive feeds resulted in the user making positive posts.
The team concluded its study by saying that emotions are spread via contagion through social networks.
The study appeared in the June edition of the journal Proceedings of the National Academy of Scientists (PNAS) under the title: Experimental evidence of massive-scale emotional contagion through social networks. According to the researchers:
Emotional states can be transferred to others via emotional contagion, leading people to experience the same emotions without their awareness. We provide experimental evidence that emotional contagion occurs without direct interaction between people (exposure to a friend expressing an emotion is sufficient), and in the complete absence of nonverbal cues.”
Facebook was publicly condemned when it became known that it conducted this Orwellian thought policing on unsuspecting users. The attack against Facebook worsened when it was discovered that one of the researchers of Facebook’s mind control study, Jeffrey T. Hancock of Cornell University, also received funding from the DoD’s Minerva Research Initiative to conduct a similar study entitled “Modeling Discourse and Social Dynamics in Authoritarian Regimes”.
Additionally, Cornell University was engaged with the Minerva Initiative and had a study funded through 2017 managed by the US Air Force Office of Scientific Research, which aimed to develop an empirical model “of the dynamics of social movement mobilization and contagions”.
The project aimed to determine the “critical mass” (tipping point) of social contagions by studying their “digital traces” in the cases of “the 2011 Egyptian revolution, the 2011 Russian Duma elections, the 2012 Nigerian fuel subsidy crisis and the 2013 Gazi park protests in Turkey.”
Facebook’s social contagion scandal also illustrates the disturbing ease that US educational facilities have in cooperating with the US military in experiments on human subjects without their knowledge or permission, in violation of ethical standards and protections.
DoD & the Minerva Initiative
The stated goal of the Minerva Initiative is to improve DoD’s basic understanding of the social, cultural, behavioral, and political forces that shape regions of the world of strategic importance to the U.S. The program seeks to achieve this by sponsoring research designed to bring together universities, research institutions, and individual scholars. In 2008, the project was provided $50 million by the United States Department of Defense. The journalist Nafeez Ahmed has expressed concern that Minerva research, in its effort to understand mass mobilization, may be targeting peaceful activists, NGOs and protest movements.
Social Network Analysis (SNA) & Unconventional Warfare (UW)
According to LTC Glenn Johnson, CW4 Maurice Duclos, Mr. Dan LeRoy in their article tittled: Mapping the Human Terrain: Applying Social Network Analysis (SNA) to an Unconventional Warfare (UW) Framework:
“Without a detailed understanding of the human terrain the Unconventional Warfare (UW) planner is uninformed about key aspects of the operating environment. SNA can provide the human terrain map needed to plan and execute UW operations. By developing a map of the human domain, SNA helps provide a description and picture of the resistance, opposition, or neutral entities, and can uncover how the population is segmented and how members interact with one another. SNA focuses on people’s behavior and how it is profoundly affected by their ties to other people and the social networks in which they are embedded.
Using SNA provides visualizations of people within their social spaces and assists in ranking their potential ability to influence those social spaces. This provides an understanding of the organizational dynamics of a resistance, insurgency, or counterinsurgency and highlights how to best influence, coerce, support, attack or exploit them. Collecting human terrain data to support SNA must be driven by commanders through focused efforts and should be conducted during every engagement with a foreign country.”
Examples of Social Network Analysis (SNA) & Unconventional Warfare (UW)
The US funded National Endowment for Democracy (NED), which is credited for numerous destabilization efforts in NAM nation states under the guise of “democracy” or imperialist subjugation as it is better known and practiced, has some great information in its numerous articles discussing the tactical use of social media to fight proxy wars. Only in the examples it provides and resources it cites, just the Chinese and Russians and NAM nation states utilize this technology. NED remains absolutely silent on its US sponsor’s activities.
According to a brief prepared by Dean Jackson for NED through the International Forum for Democratic Studies: The velocity and volume of disinformation in the contemporary information space has amplified its effectiveness and left many members of the public increasingly angry, fearful, or disoriented. This leaves the public even more vulnerable to future manipulation, resulting in a cycle of declining public trust in objective sources of information which some analysts call truth decay.
According to NED, effective ways to use social media as an unconventional weapon in proxy wars is to:
-
React or create crisis by flooding information space and drowning out discussion via online trolling, harassment, and distraction, especially with highly active automated accounts. These techniques push independent voices out of public spaces and are can be considered a new form of political censorship.
-
Falsify evidence, push misleading narratives, and spread falsehoods. Use media and diplomatic resources concurrently to promote false stories at times of rising anti-government sentiment.
-
Create accounts that are partially automated and partially controlled by human users to avoid detection. These are often referred to as cyborg or sock puppet accounts.
-
Use preexisting divides within target societies to produce content for which there is societal demand. Disinformation is more effective when it’s amplifying existing political beliefs and divisions, as opposed to introducing new narratives into the public sphere.
-
Use proactive disinformation campaigns to achieve real-world impact by influencing the actions of consumers.
-
Use disinformation around elections to influence citizens’ decisions to vote or to abstain from voting.
-
Use disinformation to promote a larger narrative over time or to degrade civic discourse by promoting division or cynicism.
Role of Social Media in Arab Uprisings
In an article by Heather Brown, Emily Guskin and Amy Mitchell titled: the Role of Social Media in the Arab Uprisings they state that the Arab uprisings could be deemed
“Facebook or Twitter revolutions” as the news media focused heavily on young political opposition protesters mobilizing in the streets, armed with smartphones.
“As almost immediately after the Arab uprisings began, there was debate over the role and influence of social media in the ouster of Tunisian president Zine El Abidine Ben Ali and the overthrow of Mubarak. “Social media indeed played a part in the Arab uprisings. Networks formed online were crucial in organizing a core group of activists, specifically in Egypt. Civil society leaders in Arab countries emphasized the role of the internet, mobile phones, and social media in the protests.”
Reality becomes distorted when all social media reference points endlessly repeat the same message concurrently. Within this context, civil unrest is born out of social contagion frenzy. An Egyptian man, who was a student protestor against Mubarak in 2011, confided in me that a crescendo of social media chatter goaded him into taking part in the protests. While he had been beaten by Mubarak’s police in an earlier incident and had personal reasons to protest, he still believes he was driven and manipulated through social media – especially since the locations to which he and his friends were led were followed by film crews and riot police too quickly after their arrival to have been un-staged.
Looking back, he now regrets taking part in the protests, as the removal of Mubarak created a power vacuum that led to greater economic and social struggle, and allowed imperial powers to take advantage of Egypt’s resources.
Personal Account of Facebook’s use of Unconventional Warfare (UW)
On April 18, 2018, I witnessed the Facebook Nicaragua expatriate groups I belong to transform its sleepy pages, that focused on advertising the best music and drink specials in town, to revolutionary pages seeking to overthrow the democratically elected sovereign government of Nicaragua.
Having just returned from Nicaragua two weeks earlier, after spending two peaceful months in San Juan Del Sur, I was shocked at the sudden and widespread vitriol controlling my newsfeed. First, I read how the government was corrupt in making changes to their social security system, and then I read how the government was murdering protestors. I knew from my understanding of Nicaragua’s history; President Ortega’s longstanding commitment to the country; its highly successful model of community policing; and the international context Nicaragua is forced to operate in due to repressive IMF loans and trade agreements, that there was more to this story.
Yet, there was no analysis anywhere to be found, only baseless accusations from predominantly white men and an occasional white woman living in Miami, Texas and Costa Rica. A number of Latinos from various locations in the United States later joined in the chatter claiming they were born in Nicaragua and thus justified in posting hostilities, when engaged in debate.
Property owners I personally knew also spoke against the government and joined in with inflammatory remarks. It is important to understand that President Ortega and the FSLN did not conduct purging campaigns to remove its bitter rightwing enemies/Somozistas. Under President Ortega’s compassionate and practical leadership, Nicaragua even forgave the Contras that its FSLN fought against once they agreed to lay down their arms.
Everywhere I looked the message of hate was the same, be it Facebook, Twitter or mainstream news media from the mouths of rightwing senators Marco Rubio and Ileana Ross-Lehtinen who staged meetings with protestors as well as alternative media such as Democracy Now and the Guardian. The understated president, Daniel Ortega, went from being an astute and beloved aged revolutionary hero to a merciless dictator in social media and the press within a few hours. The news feed was so similar, overwhelming, relentless and well packaged, that it seemed immediately like an expertly orchestrated massive disinformation campaign set by the imperial United States to remove President Ortega and the FSLN from office yet again.
Anytime I questioned the prevailing narrative on the Facebook expatriate groups, 10 to 15 users, with questionable profiles, ganged up on me. I was personally insulted, told to remove my posts, and threatened. They feared my comments. Additionally, my Facebook friends were contacted and insulted and told to “make me remove my posts”. I received phone calls on Facebook Messenger despite the fact that my friend’s list is hidden.
The questionable profiles that contacted me often listed present employment with an obscure non governmental organization (NGO), and/or prior employment with the US State Department, US military, or in one case a user listed his job as a “private investigator” that just returned from “doing security in Venezuela.”
Yet, what was most troubling to me was that people I knew from San Juan Del Sur were brainwashed by the massive and unrelenting wave of disinformation. PSYOPS temporarily worked. They began repeating hostile catch phrases against the government as if it was Holy Scripture. They would not read or watch anything in favor of the government, despite my best efforts through verbal and written communication. They made up their minds, based on social media and Google’s distorted reality, that revolution was what the majority of people in Nicaragua wanted. This distortion couldn’t be farther from the truth, as President Daniel Ortega was elected with over 70 percent of the vote. However, the barrage of repeating fake propaganda videos resulted in social contagion frenzy, similar to that experienced by the Arab students in Egypt.
As it turned out, many of the photos and videos posted and used to incite violence were actually taken in Mexico and Honduras years earlier and many of the “dead” were found resurrected in other parts of Nicaragua alive and well. However, armed criminal mercenaries called “peaceful student protestors” by the news and social media did murder police and civilians. Fortunately, distorted reality can only last a short time.
In Nicaragua, the government had control over the county within three months, as the news and social media lies became apparent to citizens and foreigners. Essentially, the criminal mercenaries that infiltrated the protests were not content to restrict their activities to the ones dictated by their US government employers. To supplement their wages, they robbed, raped and pillaged the communities to which they held hostage, and were systematically removed by local residents as well as the police.
Facebook’s Biased Reaction
Facebook automatically flagged and blocked my posts on Nicaragua’s expatriate groups, and group administrators removed the ones that slipped through. My posts merely explained the US government’s longstanding disinformation campaigns against Nicaragua. Then, Facebook and/or group administrators removed my access to the pages. Eventually, due to threats, I deleted my Facebook profile. However, PSYOPS did not succeed in silencing me; instead, it encouraged me to write for a larger audience.
Control over Dissent Using Facebook
In late July 2018, I created a new Facebook profile and began again to monitor Nicaragua expatriate news groups and post articles that support its sovereign government against slanderous untruths. On July 29th, Facebook removed and considered spam two articles that I posted: “The Case Against Daniel Ortega” by Chuck Kaufman hosted on the Libya360.Worldpress.com website and “Opposition Beyond the Violence in Nicaragua” by John Perry hosted on The Guardian website. Both articles non-violently support the sovereign government of Nicaragua. Fortunately, I was able in both instances to get the posts restored after clicking a few buttons. Yet I still remain unable to get Facebook or group administrators to remove articles that promote violence against the government. Despite my flagging of these fake articles for deletion under the Facebook categories: terrorism, violence, harassment, and hate speech, Facebook allows this vitriol to remain.
After posting a third article titled: “After the Failed Coup, After All the Lies, Nicaragua Rebuilds” by Tortilla Con Sal, hosted on the Telesur website, Facebook locked me out of my user account. The article I posted promoted peace and reconstruction. For the record, none of the articles I posted were ever in violation of Facebook’s community standards.
To unlock my user account, Facebook required me to upload a close-up photo of my face. Facebook’s clear bias against the content of my posts coupled with its desire to invade my physical privacy proved intimidating. Facebook, a corporate behemoth, had me vulnerable and exposed, as I could not access my account to delete it without first revealing my personal identity. Facebook is like the mighty Wizard of Oz in that its master is concealed behind a curtain and unreachable. Facebook lists no email address or phone number for “customer service”.
Did Facebook’s version of Orwell’s Thought Police flag my account? After a few deep breaths, I took a chance that Facebook would use its facial recognition software to confirm my physical identity against an Internet search. So, I found a close-up photo online that corresponded with the fake name I used to open my Facebook account, and uploaded it hoping for the best. It worked. I had access to my profile by the next morning. However, I continue to wonder if Facebook was fooled or if I am merely being given more opportunity to violate the Patriot Act in thought and word? Are my CIA, NSA, FBI and DoD “friends” continuing their surveillance of my personal communications on Facebook’s Messenger and WhatsApp applications just more closely? Under the Patriot Act, Facebook is mostly prohibited from disclosing law enforcement surveillance. According to Facebook, in its summary of its 2017 transparency report, it states:
“The US government requests for account data remained roughly even at 32,742, of which 62% included a non-disclosure order prohibiting Facebook from notifying the user, which is up from 57% during the first half of 2017.”
Other transparency report findings of note for Google, Verizon and AT&T are as follow:
“Google received 48,941 government data requests affecting 83,345 user accounts in the first six months of 2017.” And, “In the reporting period between 2016 and 2017, local, state and federal government authorities seeking information related to national security, counter-terrorism or criminal concerns issued more than 260,000 subpoenas, court orders, warrants, and other legal requests to Verizon and more than 250,000 such requests to AT&T.”
On May 24, 2018, the ACLU filed a Freedom of Information Act request to find out how agencies like the FBI and the Department of Homeland Security are collecting and analyzing content from Facebook, Twitter, and other social media sites.
“Government surveillance of social media can have serious consequences, whether you’re a U.S. citizen, a lawful resident, or are seeking to immigrate to or visit the United States. The FBI appears to be using social media as a basis for deciding who to interview, investigate, or target with informants or undercover agents. A single Facebook post or tweet may be all it takes to place someone on a watch list, with effects that can range from repeated, invasive screening at airports to detention and questioning in the United States or abroad.”
With the proliferation of US government non-discloser surveillance, the use of facial recognition software, and the requirement to upload close-up photos to gain access to existing profiles, the velvet gloves are completely off Facebook as an iron fisted US government spy tool. The justification that this intrusive level of policing is merely to remove “fake profiles” doesn’t fly. There are alternate methods that do not compromise our constitutional and civil rights. This is a ruse, engineered by the NSA. Be warned.
Facebook Facial Recognition Software and the US National Security Agency (NSA)

As discussed by James Risen and Laura Poitras in their May 31, 2014 article titled: N.S.A. Collecting Millions of Faces From Web Images, the National Security Agency (NSA) is actively harvesting massive amounts of images of people from communications that it intercepts through its global surveillance efforts for use in sophisticated facial recognition programs, according to top-secret documents.
“The spy agency’s reliance on facial recognition technology has grown significantly over the last four years as the agency has turned to new software to exploit the flood of images included in emails, text messages, social media, videoconferences and other communications, the N.S.A. documents reveal. The agency intercepts millions of images per day including about 55,000 facial recognition quality images which translate into tremendous untapped potential, according to 2011 documents obtained from the former agency contractor Edward J. Snowden.”
In-Q-Tel (IQT)
In early 1999, with funding directed by the US Central Intelligence Agency (CIA), input from Silicon Valley consultants and Norman Augustine, a former CEO of Lockheed-Martin, In-Q-It, a non-profit corporation was formed. Its core mission to improve the data collection and analysis capabilities of the CIA through access and control over emerging Information Technology (IT) remains intact to date. By March of 1999, the corporation received its first contract. In 2000, its name was changed to In-Q-Tel (IQT).
IQT invests in areas where there is both a CIA need and private sector interest. Examples of commercial applications that also support intelligence functions are: data warehousing and mining, knowledge management, profiling search agents, geographic information systems, imagery analysis and pattern recognition, statistical data analysis tools, language translation, targeted information systems, mobile computing, and secure computing.
Though IQT, the CIA has the option of purchasing products directly from the vendor or launching Research & Development (R&D) projects. While IQT’s present budget remains secret, its first year budget was $28 million. According to a 2013 Fox Business News report, IQT claims that for every dollar it invests in a company, the venture community invests over $9. Further, it claimed that it had leveraged more than $3.9 billion in private-sector funds.
R&D remains the core of its activities. Sometimes IQT assembles teams of companies to create the solution it seeks; other times it is a co-investor in a fledgling company with additional business partners. IQT also uses request for proposal. Essentially, IQT is empowered to use whatever model meets its objective.
In the area of R&D, the CIA’s agreement with IQT allows it and/or its partners to retain title to the innovations created, and to freely negotiate the allocation of Intellectual Property (IP) derived revenues. The only major stipulation is that the CIA retain traditional “government purpose rights” to the innovations. This agreement has allowed IQT to amass considerable financial resources secretly over the last nineteen years since its inception. Also, this agreement has permitted collaborating and beholden individuals to become extremely wealthy and powerful.
To restrict contracting to specific entities, and to achieve privacy from oversight authorities, IQT uses DARPA’s contract model called “Other Transactions” (OT). OT contracts enable IQT to bypass Federal Acquisition Regulations (FAR), which requires competition in federal contracting.
Because of the clandestine nature of IQT’s work and its key relationship to the CIA, both entities remain extremely vulnerable to security risks during solution transfer.
Origin of Facebook
While no record of the CIA directly funding Facebook through IQT is apparent, members of IQT’s top management are founding members and/or board members of Facebook. Some of Facebook’s allure to users is that Mark Zuckerberg and his friends started the company from a Harvard dorm room and that he remains the chairman and chief operating officer. If he didn’t exist, he would need to be invented by Facebook’s marketing department. Primarily, the legend and image of a fresh faced Zuckerberg provides a palatable context that entices young people to voluntarily part with their constitutional right to privacy for social acceptance. Though subtle coercion, young people come to believe that in order to be “liked” by their peers, they need to be part of the Facebook brand.
A few months after Facebook was formed in 2004, it received its first capital injection from Peter Thiel, a member of the Steering Committee of the exclusive Bilderberg Group, the drivers of globalization. Members include political leaders, key members from the intelligence community, and experts from industry, finance, academia and the media. According to Global Research’s Stephen Lendman, in his May 2014 article titled: The True Story of the Bilderberg Group and What they May Be Planning Now:
“Bilderbergers want to supplant individual nation-state sovereignty with an all-powerful global government, corporate controlled, that’s check-mated by militarized enforcement.”
In August of 2004, Thiel acquired a 10.2% stake in Facebook for $500,000. The next two capital injections were $12.7 million from Thiel and Accel Partners in May 2005 and then $27.5 million from an Accel-led round of financing that included Thiel, Accel and Greylock Partners in April 2006. In 2012, Thiel sold the majority of his shares for over $1 billion, but remains on the board of directors.
Essentially, IQT is linked to Facebook through Thiel, and Thiel is linked to IQT through his firm Palantir. So, to understand Facebook it is first necessary to understand Palantir, then Thiel.
Palantir
According to Wikipedia, Palantir was started in 2004. Its only outside backer was the CIA’s nonprofit venture capital firm, IQT. Through pilots facilitated by IQT with computer scientists and analysts from intelligence agencies, Palantir’s technology was developed over a three-year period. A document leaked to TechCrunch revealed that Palantir’s clients as of 2013 included at least twelve groups within the U.S. government, including the CIA, DHS, FBI, CDC, the Marine Corps, the Air Force, Special Operations Command, West Point, the Joint Improvised-Threat Defeat Organization and Allies, the Recovery Accountability and Transparency Board and the National Center for Missing and Exploited Children.
Peter Thiel
According to Wikipedia, Peter Thiel was born in Germany and holds German, American and New Zealand citizenship. Besides being a member of the Bilderberg Group’s Steering Committee as referred to earlier, Thiel is the co-author of an anti-multicultural book titled “The Diversity Myth: Multiculturalism and Political Intolerance on Campus”, where his racist and misogynist bias is apparent in his argument that multiculturalism in colleges is hurting education and that some cases of alleged date rape are actually seductions that are later regretted.
Despite his apology, issued 20 years after the book was published, he gave $1.2 million to the campaign of then Republican presidential nominee Donald Trump, who ran on a white nationalist campaign. Thiel is also is a member of the super PAC called: Make America Number 1. The super PAC is credited with donating funds to Steve Bannon, via a shell company he heads named Glittering Steel. Bannon is widely considered a racist, anti-Semite and white nationalist. The supper PAC also donated funds to rightwing Senator Ted Cruz. With Thiel’s clear intent and bias, it should be no surprise that the Facebook Cambridge Analytica scandal favored Trump in the election, and that the violent prevailing narrative against Nicaragua, supported by Ted Cruz, is impossible to remove from Facebook’s expatriate group pages.
Accel Partners: In 2004, Accel partner James Breyer sat on the board of directors of military defense contractor Bolt, Beranek and Newman (BBN) with IQT’s CEO Gilman Louie. BBN is known for essentially helping to create email and the Internet for the DoD. Breyer is a member of the Council on Foreign Relations.
Greylock Partners: Howard Cox, the head of Greylock, served on IQT’s board of directors. Before Greylock, Cox served two years in the Office of the Secretary of Defense.
Origin of Google
Launched in 1998, Google is one of the world’s largest media companies. While the Department of Defense (DoD), CIA, NSA and Google’s marketing department would like users to believe that its founders, Stanford University students, Larry Page and Sergey Brin developed software independent of the DoD, the truth is they didn’t. They were both on the payroll of the National Science Foundation (NSF) while working on its Stanford Digital Library Project (SDLP). This library project is similar to Google in that it involved the creation of search algorithms to scan large quantities of data to find relationships.
The NSF is funded by the US federal government and expresses in its mission statement its intention to “secure the national defense”. NSF has a longstanding relationship with the DoD’s Defense Advanced Research Projects Agency (DARPA). Nothing requiring serious funding and real paychecks involving Information Technology and US Universities is done without DARPA knowledge as detailed below:
“In the 1970s, the agency responsible for developing emerging technologies for military, intelligence, and national security purposes the Defense Advanced Research Projects Agency (DARPA) linked four supercomputers to handle massive data transfers. It handed the operations off to the National Science Foundation (NSF) a decade or so later, which proliferated the network across thousands of universities and, eventually, the public, thus creating the architecture and scaffolding of the World Wide Web.”
Not only was Google’s development nurtured by NSF/DARPA, but Google was also was aided by the secretive Massive Digital Data Systems (MDDS) program which was administered by private contractors for the CIA and NSA. The MDDS program sought to identify the digital fingerprints of users inside the World Wide Web so information requests could be tracked, sorted and aggregated to reveal individual proclivities and that of like-minded others with the intention of assembling target groups for easy surveillance so as to predict and counter their plans. The MDDS project was named Birds of a Feather with the thinking that like-minded individuals will engage in coordinated action together, just as birds fly in predictable V-formations. Predictability is key to the CIA in its efforts to weaponize social unrest. MDDS is considered to have helped create the design breakthrough that Google was built upon
Google has been an obvious partner with the CIA since 2004 when the company bought Keyhole from IQT, the CIA’s venture capital nonprofit. EarthViewer, Keyhole’s mapping technology software, became Google Earth.
Google and Social Media’s Influence
Besides geographic and locational tracking, Google assists the government in its efforts to write, and rewrite, history. According to its Google’s transparency report, the US government has named 79,901 items for removal since 2009. To add perspective to this number, consider that for this same period in time, Venezuela has named 10 items for removal, and Nicaragua has named 1 item for removal.
Content Placement in Social Media and Google
Olivia Solon and Sam Levin detail, in their December 16, 2016 article for The Guardian, How Google’s Search Algorithm Spreads False Information with a Rightwing Bias. According to the authors, search and autocomplete algorithms prioritize sites with rightwing bias, and far-right groups trick it to boost propaganda and misinformation in search rankings. As described below, the authors uncovered this bias in environmental as well as social and political examples:
“Following a recent investigation by the Observer, which found that Google’s search engine prominently suggests neo-Nazi websites and anti-Semitic writing, the Guardian has uncovered a dozen additional examples of biased search results. Google’s search algorithm and its autocomplete function prioritize websites that, for example, declare that climate change is a hoax, being gay is a sin, and the Sandy Hook mass shooting never happened.”
To test this allegation out, I entered the following text: “Socialism is…” Autocomplete added: “…is for figs.” The full sentence with autocomplete then read: “Socialism is for figs.” Photos of a red t-shirt appeared. On the t-shirt is a drawing of Che Guevara, a limp wrist, and text. Upon review, I found that an extreme rightwing group is marketing this t-shirt. The word “figs” in the text is written with a missing “I” that is replaced with the drawing of a fig hanging from a tree branch. Because of drawing of a limp wrist, this text can be interpreted by the reader to mean that socialism is for “fags.” In the US, the word “fag” is a derogatory name for homosexuals, and a limp wrist is a derogatory symbol. This supports the Guardian’s observation of Google’s bias against homosexuals as well its bias against socialists. Additionally, the fig fruit represents the name of the village in Bolivia where Che Guevara was captured and murdered. Thus, the fig represents a death threat against socialists. Hopefully, a socialist cyber activist can remove this blight against a beloved revolutionary hero.
Google’s Influence in Elections
As explained by Robert Epstein, from the American Institute for Behavioral Research and Technology, Google has the power to rig elections through something he calls the search engine manipulation effect (SEME). Based on his four years trying to reverse engineer Google’s search algorithms, he concludes that:
“We know that if there’s a negative autocomplete suggestion in the list, it will draw somewhere between 5 and 15 times as many clicks as a neutral suggestion,” Epstein said. “If you omit negatives for one perspective, one hotel chain or one candidate, you have a heck of a lot of people who are going to see only positive things for whatever the perspective you are supporting. Even changing the order in which certain search terms appear in the autocompleted list can make a huge impact, with the first result drawing the most clicks, he said.”
Appearing on the first page of Google search results can give websites undue authority and traffic.
“These platforms are structured in such a way that they are allowing and enabling, consciously or unconsciously, more extreme views to dominate,” said Martin Moore from Kings College London’s Centre for the Study of Media, Communication and Power.”
Epstein believes these two manipulations work together and have a profound impact on people, since they are unaware it is being done. He believes this is compounded by Google’s personalization of search results. This means users see different results based on their interests.
According to politico.com, the problem is that more than 75 percent of all online searches in the United States are conducted on Google. Thus, if Google’s CEO, a rogue employee or the search algorithm favors one candidate, there is no way to counteract that influence. Politico’s research shows that even when people do notice they are seeing biased search rankings, their voting preferences still shift in the desired directions toward the bias. It’s as if the bias is serving as a form of social proof. The thinking is that if the search engine prefers one candidate, that candidate must be the best. Biased rankings are hard for individuals, regulators and election watchdogs to detect as SEME is easy to hide through customized search results.
In Wired’s 2010 article titled: Exclusive: Google, CIA Invest in ‘Future’ of Web Monitoring, it discusses the company Recorded Future, that is funded by both the CIA’s IQT non-profit and Google. Both IQT and Google Ventures have seats on Recorded Future’s board. Not only does the software, Recorded Future, scour websites, blogs and Twitter accounts to find the relationships between people, organizations, actions and incidents in the present, but also in the future. In looking at the invisible links between documents that mention similar or related entities and events, it can figure out the participants, the location, and predict when it might occur. According to Recoded Future, the software can assemble actual real-time dossiers on people. Recoded Future maintains an index with more than 100 million events.
“The cool thing is, you can actually predict the curve, in many cases,” says company CEO Christopher Ahlberg, a former Swedish Army Ranger with a PhD in computer science.”
Content Placement in Social Media and Google
Besides taking proactive security measures, activists and the NAM can benefit by controlling the technology that decides the placement of supportive material on social media and Google. As most involved in the drafting and dissemination of content already know, everything that departs from the prevailing imperialist narrative is automatically considered subversive and blocked. While quality content continues to exist, locating it on the Internet is like finding a needle in a haystack, even when one already knows what is being sought, by whom, and from where.
The latest trick is for a news item of interest to be blocked by a message warning of an “expired security certificate” and threatening “a virus upon opening”. This was found on an article titled: Cyber warfare: Challenge of Tomorrow, by none other than Counterpunch’s plagiarist spy Alice Donovan.
The Cost of US Cyber Warfare
The United States 2019 proposed intelligence budget at $73 billion has nearly doubled since 2005. This figure includes the National Intelligence Program (NIP) budget at $54.6 billion and Military Intelligence Program (MIP) budget at $18.4 billion. Back in 2005, there was no MIP budget. The total NIP Budget was $39.8 billion, which is still an exorbitant amount of money.
The NIP funds Intelligence Community (IC) activities in six Federal Departments and two independent agencies: the Department of Defense, the Department of Justice, the Department of Homeland Security, the Department of State, the Department of Energy, the Department of Treasury, the Central Intelligence Agency, and the Office of the Director of National Intelligence.
As described in by the Washington Post in its article titled: “The Black Budget”, the CIA, NSA and National Reconnaissance Office (NRO) received more than 68 percent of the 2013 black budget. The CIA received $14.7 billion, the NSA $10.8 billion, and NRO $10.3 billion. Within its funding mission categories, $20.3 billion was for Warning U.S. leaders about critical events and $17.2 billion was for Combating Terrorism.
In looking at the new 2019 MIP budget, one can better understand how new initiatives and training in cyber warfare are being funded. Take for example the US Air Force Cyberspace Defense Operations (IB4X1) Summary description:
“Personnel in the Cyber Warfare Operations specialty perform duties to develop, sustain, and enhance cyberspace capabilities. These capabilities are used to defend national interests from attack and to create effects in cyberspace to achieve national objectives.” “They conduct both offensive and defensive cyberspace operations. They act to protect cyberspace systems from adversarial access and attack. They execute command and control (C2) of assigned cyberspace forces and de-conflict cyberspace operations. They will partner with Department of Defense, interagency, and Coalition Forces.”
While the US government clearly takes the lead in unconventional warfare technology, due to its massive resources and funding, it leaves in its wake tons of technological opportunities ripe to be exploited. What can’t be appropriated can be protested. Just don’t post anything tactical on the Internet or use smart phones, because your “friends” in the US government are watching. Take heart, this elaborate surveillance system was devised because the ruling elite is outnumbered. Knowledge is power.
Lauren Smith, author of historical fiction, has a BA in Politics, Economics and Society from SUNY at Old Westbury and an MPA in International Development Administration from New York University. Her novel on Nicaragua’s 1979 revolution is due out in 2019.
Originally published at Wrong Kind of Green. Republished under a Creative Commons Attribution-NonCommercial-NoDerivs 3.0 Unported License.