Editor’s note: republished under a Creative Commons License, this article is “A handful of digital security things that that most of us should do almost all of the time,” in the words of the author. We offer it here as a resource for activists who wish to communicate securely, to protect their groups and allies against digital infiltration or monitoring. by John Scott-Railton
This is not intended as a comprehensive security guide. Nor is it a privacy guide. There are many security guides online. It is not intended for people who think they are currently hacked. Or who are trying to remain anonymous. Or hide their browsing or e-mail traffic. Suspect you are currently under attack? Have a look at the last section of the document.
“Hey this is really simplistic!” Yes! Read why in the FAQ.
ONE WEIRD TRICK HACKERS HATE? 2 STEP AUTHENTICATION
Why: Two step verification is a great way to increase the security of your account. In its simplest form, it works by sending you an SMS with a code after you have entered your password. You need this code in order to log in.
Time commitment: 5-10 minutes
This means that even if someone has stolen your password, they won’t be able to access to your account.
Here are some directions for setting up 2 step verification on your different accounts:
For a more comprehensive list of all services offering 2 Step Authentication, click here
2 Step to the Next Level
Getting SMSes every time can be cumbersome. Before you throw up your hands with frustration, you should know that are apps that make the process easier. They also make it much more secure. The most widely used is the Google Authenticator.
Let Google walk you through getting the Authenticator App.
If you are seriously concerned about security, there is an even more robust option: Security Keys. These small USB dongles give you all the benefits of 2 Step authentication, but can’t be hacked. They don’t cost much, and are a dramatic improvement.
Learn more about security keys, and where to purchase one.
YOUR PHONE  Source: USAID Phone encryption Why: when your phone is encrypted only you or someone who has your password can access the data on the device. It is fully effective only when the device is turned off.
Source: USAID Phone encryption Why: when your phone is encrypted only you or someone who has your password can access the data on the device. It is fully effective only when the device is turned off.
Time commitment: 5 minutes to set up, 20-60 minutes of time for your phone to do its thing.
Special requirements: plug your phone in
Android Step 1: Set a good password
Step 2: Encrypt it! Here is a guide on how to encrypt your android phone iPhone
The neat thing is that your iPhone is encrypted by default. It would be cool if Androids did this, right? But for it to ‘count’ you should use a strong password, rather than a simple pin. A guide on encryption of your iPhone Note: Encryption is not available on iphones older than 3GS
*Reminder: If the phone is hacked this doesn’t solve the problem since a hacker can already look at your data*
Talk and Text With Some Privacy  Source: Open Whisper Systems Why: when your communications are properly encrypted, only someone with access to a side of the conversation (like your phone, or your friend’s phone) can listen in.
Reminder: If the phone is hacked this doesn’t solve the problem since a hacker can already read everything Time commitment: 2 -5 minutes to download and verify the app to your number.
Source: Open Whisper Systems Why: when your communications are properly encrypted, only someone with access to a side of the conversation (like your phone, or your friend’s phone) can listen in.
Reminder: If the phone is hacked this doesn’t solve the problem since a hacker can already read everything Time commitment: 2 -5 minutes to download and verify the app to your number.
Note: This app provides secure SMS-like messaging and calls over data. This option requires data plan to work, and it does not hide the fact that you are making these communications!
Android: Signal Private Messenger for Android iPhone: Signal Private Messenger for iPhone
What about my favorite chat app?
Signal is great, and easy to use. It is a drop-in replacement for existing call and messaging features, as long as you have good data service! But there are many other tools that have other features, advantages, and quirks. Including a few, like WhatsApp, that use the same encryption protocol as Signal. You may find it hard to move all your contacts over to Signal, but easier to get everyone to agree to use WhatsApp. So, what to do?
To sort through it all the Electronic Frontier Foundation (EFF) has done a great job assembling information about the security and privacy policies of many different chat apps. Have a look here. Note: As of January 2017 EFF is re-developing the Secure Messaging Scorecard. Check back often for the new version. Something to keep in mind Phones send out a lot of information about you that you can’t control easily. Even if you take the steps here there is no guarantee that you are controlling what the phone shares with various parties, or to prevent malicious actors from gaining access to your phone.
YOUR COMPUTER  Source: U.S. Fish and Wildlife Service. Updates
Source: U.S. Fish and Wildlife Service. Updates
We all hate updates. But they go a long way towards keeping you safe. If you find updating as painful as everyone else, you might consider Secunia PSI, which manages updates for you. There is a free version available for Windows only here that will take *some of the pain out*.
Drive Encryption  Image via Apple
You should encrypt your personal and professional laptops and computers. This means that when they are turned off your data can’t be accessed without your password, or a lot of work. This doesn’t work as well when the device is in Sleep or Hibernation mode.
Image via Apple
You should encrypt your personal and professional laptops and computers. This means that when they are turned off your data can’t be accessed without your password, or a lot of work. This doesn’t work as well when the device is in Sleep or Hibernation mode.
Time commitment: 5-10 minutes to set up. Then a restart. Then a wait (sometimes you can do other things) while your computer encrypts. Plug in laptops before getting started.
Windows
Some Windows versions support BitLocker encryption. Many don’t. Here is a guide to BitLocker (The guide link addresses some cases where your version does not support it.). Have a look at veracrypt if your Windows does not have BitLocker.
Mac OS
All recent Mac computers support encryption using a built-in feature called FileVault. Here is a guide to FileVault Secure Communication
There are a lot of things to consider before choosing a secure communications solution for your computer. I encourage you to consult some more systematic resources like the many security guides online to make a selection.
That said, Signal Private Messenger has an excellent Chrome Extension that you can use to message securely from your desktop.
 Signal Messenger on Chrome is awesome, and free. Image: Open Whisper Systems Time Commitment: 1 minute to set up
Signal Messenger on Chrome is awesome, and free. Image: Open Whisper Systems Time Commitment: 1 minute to set up
Chrome Browser Install Signal Private Messenger for Chrome Passwords. Ugh!
Nobody likes passwords. Except hackers, who thank you in advance for using the same password for many things
Get a Password Manager
A neat trick to avoid having to re-use your passwords is to get a password manager and let it do the heavy lifting.
Here are some password managers reviewed by lifehacker.
Password Alert!
This new tool, made by Google, will check where you enter your Gmail password and warn you if you are being tricked by a website into entering your password in the wrong place. It is available as a Chrome extension.
Time commitment: 3-5 minutes
Install Password Alert from here
How can I be safer looking at messages?
Gmail and the Outlook Web App both have a fantastic feature: you can preview attachments without opening them on your machine. If you discipline yourself to do this regularly you will make it a lot harder for someone to hack your machine.
Spot A Malicious Message Why: A very, very common route into computers is via emails and messages containing malicious attachments and links. Those links can deliver viruses that undo all of your other security measures.
These messages are based around trying to trick you into performing some behavior. These work with things like:
- FEAR Making you afraid (oh no, I need to change my password!)
- URGENCY Making you worried that something is urgent
- CURIOSITY Making you curious (what is this e-mail about? I will click the link..)
- ENTICED Enticing you (important message about a political issue)
These messages can be very sophisticated. Sometimes they also come by SMS or by messages on Skype, WhatsApp etc.
Not sure whether you are able to recognize them? Take an online quiz and see how you do. Nitpick: the examples from the quiz are not as fancy as some of the attacks we’ve observed.
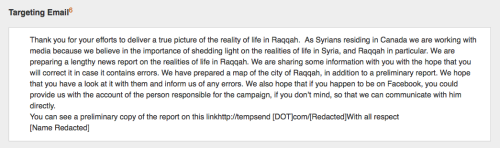 Source: ISIS! This is an example to show how personalized a dedicated attacker can be. Click on the image to read the report. I think I spotted a malicious message…what do I do? Step 1: If you want to have a look at the file Examine an Attachment Preview the attachment with Gmail or with Outlook Web. This lets you view it without being infected.
Source: ISIS! This is an example to show how personalized a dedicated attacker can be. Click on the image to read the report. I think I spotted a malicious message…what do I do? Step 1: If you want to have a look at the file Examine an Attachment Preview the attachment with Gmail or with Outlook Web. This lets you view it without being infected.
- Came to a different inbox where you can’t preview it? Forward it to your Gmail or Outlook and preview it there
If it doesn’t preview or the content looks suspicious, consider Step 2. Double Check a Link Don’t click the link! Instead right-click it, copy the link and paste it into your browser or somewhere else if it is long. Look at it before hitting the enter key.
First, look at the name of the website, especially the part right before “.com,” or whatever the “.ending” is . Is the name spelled correctly? Does it match the page you want to visit?
- For example: “https://google.secure-mymil.com” is not a Google website! It is secure-mymyel.com, which could be fake. Now look at https://mail.google.com, which genuine. See the difference? The correct website name, “google.com” is right before the “.ending.”
If the website name looks right, check for the at the beginning “S” in “HTTPS://.”
- The “S” stands for “Secure” and means that your connection is being encrypted
Step 2: Six Second Detective
Upload a suspicious file to www.virustotal.com to get an answer. Go to the website and upload the file.
Check a suspicious link by pasting it into www.virustotal.com.
- You can also check the link against a reputation service ( click here for a list).
Privacy Tip: files submitted to VirusTotal are available to security researchers. Make sure you don’t submit sensitive things.
Step 3: I’m now convinced this is bad.
If you are working with an organization, this would be a great time to contact your IT staff. Make sure not to delete the message before contacting them!
If you are an individual, consider reaching out to someone with computer expertise. If you aren’t sure you know the right person, have a look at this website maintained by several organizations about what you can do and determine whether it makes sense to reach out.
Finally, you can always share with researchers like Citizen Lab (where I work). We can be reached at info[at]citizenlab.org.
FAQ Hey, this was really simplistic!
Yes! This document doesn’t even mention e-mail encryption. And it doesn’t give a lot of explanation for *why* you should do these things.
You can’t really do digital security without first carefully assessing your risk, then being systematic in how you address it. The objective of this document is simply to lay out things that, on balance, help. If you want something systematic there are lots of resources. Here is a curated list of online security guides. Here is another. I can’t vouch for all of the linked resources.
If you want another shortlist: this is a very interesting take on expert vs. novice security practices.


