Bitcoin = Death Processors
by Darin Stevenson / Medium
bitcoin Is Makeworky Unmoney
bitcoin is not exactly money. It’s a potentially valuable abstraction of computational ‘work’ that ‘earns’ bitcoin value. But what is bitcoin value and what is the nature of the work? The answers are bizarre because they are nonsensical.
bitcoin value is an abstraction of participation in the history of the network and its transactions. ‘Work’ is a (largely) nonuseful recomputation of, first, the transaction history of the network — which has to be reprocessed each time there is a bitcoin transaction. Then, continual banging away at some useless math with added ‘weight factor’ that makes it arbitrarily difficult for computers to accomplish the generation of a new record-set over time.
The bitcoin algorithms adjust this factor in order to require enough ersatz work so that the heartbeat of the system pulses (produces a block) approximately every ten minutes… and they scale the computational complexity accordingly via input from bitcoin’s own daily developmental activity.
By crossing an invented computational abyss, millions of computers and other machines, many of which have been secretly compromised by hacks, are working full tilt, around the clock… to simply generate a deeper abyss requiring ever-more powerful and numerous computers to cross. And this generates ‘blocks’ in an economy of numbers in machines. These numbers are not exactly money, and their actual value is more complex than cash. And the machines must be serviced, cooled, attended and backed-up, as must the results of their nearly useless hyperactivity.
Most participants are using machines specially designed to resolve these invented computational targets, and as we make faster computers to do this, the network amplifies the difficulty to throttle the pulse.
What is all this about? Well, it’s not a simple question.
Let’s start with money.
What Is Money?
To understand money, one must begin to understand its sources. Perhaps the most fundamental of such introductions is the direct and fascinated observation of animals in nature. The origins of money (and memory) are in nature; exploring them has profound implications for own developing creativity and intelligence.
Beavers, squirrels and other small creatures, including the incredibly inventive corvids, store food (and sometimes treasures) in hiding places we call caches. Some predators may also cache food briefly (meat tends to go bad or get eaten by other creatures who can sense its presence). So, too, ants, wasps, bees and other social insects. This is actually a mode of living memory.
Notice the homonomy here? Cache and cash are the same sound, and this isn’t accidental. Direct relation with nature as and through living places is the original source of our concepts of value. Our relationships with environmentally accessible resources and caching are not merely the beginning of our monetary systems, they are the probable origin point of the peculiar forms of memory and cognition that are the hallmark of our species.
We carefully cache and value our dead. And money is an abstraction of dead people, places, and moments.
Our kind of mind was born in forests and places fraught with elaborate relational constellations of biodiversity and symbiotic intelligence. Alas, the nominal treasure we acquired there went haywire, and now we have nearly wiped those places off the map and erased them from our experience. What was their replacement?
Money (and machines). A representation of cached value, extensible to nearly any common domain of exchange.
There are no living places anymore. We do not encounter or create value… we get cash. Most of the time… that means that someone, or some ecology somewhere, is being wiped out. The results are representational forms of wealth and power.
We don’t have ancient forests any more, and the futures they portended are gone. What there are, are sheets of paper, ingots of gold, diamonds, and little banks of numbers… in machines. On balance sheets.
***
Numeric Supremacy
Numbers. We keep track of them. Too often they become lethal fictions with which ‘we’ (ostensibly: our societies and their systems) determine who lives and who dies. Who is wealthy and who bereft. Everyone is identified by and for the sake of numbers. We imagine these numbers to be true, just, inviolable. But we do not really understand the valuations or applications we celebrate and avow as real; there are always many aspects of value with crucial bearing on any analysis that we leave out of our accounting. Living beings, for example. Minds.
Many of our bizarre celebrations of monetary value or obedience to statistical analyses are simply flawed. It’s hard to get reasonable statistics for any real-world situation. Sometimes we are using stats that are cripplingly outdated or merely wrong. Assays attempting to discover the (astronomical) number of birds killed by electricity transmission only counted those found near wires. What’s the actual number, or a very close guess? We don’t know, because statistics are not entirely reliable beyond their well-behaved purposive contexts. Statistics, it turns out, are very often both manipulable and conveniently monodimensional.
So, too, the cash that stands sovereign behind them.
Such ‘numbers’ and our mishandling of them partly determine or suggest to us what to believe or think about ourselves, each other… the nature of the real. They portend what resources are protected, abstracted from nature, transported or obliterated, for what purposes, and whose ‘profit’.
We seem to have a serious vulnerability as regards representations. Our peculiar fantasies about the meaning of progress or success have cast life on Earth into direct competition with their outcomes—living beings and places now compete for terrain, safety and survival directly against not only objects, habits and machines… but mere data. And they lose.
So do we.
A photograph can become so popular that hundreds or even thousands of creatures must die simply to sustain and transmit it millions or billions of times. As unthinkable as this is, it is a fact: people die because numbers in machines merit more resources, attention, care, and nurturance than living beings.
Our electronic activity and transactions have absolutely lethal real world costs that no one is paying attention to. And as we continue to invest human attention and work in an increasingly unreal electronic representation of reality, those prices become staggering. They were unsurvivable 20 years ago. Today, they are simply an ever-expanding array of new forms of environmental, social and psychological rape. For profit. And they can hide in our cultures and lives in ways that are as deadly as they are invisible.
***
When Costs Go Explosive — And Invisible
One of the statistics that is modestly important here is the present population of our species and its growth over say, the last 100 years or so. These figures project their significance on everything we do, and dramatically magnify the repercussions of our common choices simply by increasing the power and frequency of the activities that produce them. An automobile trip to the grocery store has an environmental impact that rises precipitously as populations repeating it double or quadruple.
And this is what has been happening with our population for quite a while now. Perhaps it is nearly as significant that the number of objects per person… particularly machines… has skyrocketed in developed nations. In other words: there are at least two population problems. Ours, and that represented by our machines. Most are happy to complain about the humans. Nearly no one is complaining about the machines.
I find this suspicious.
Here are some ‘interesting numbers’: the statistics of human population growth. It took us at least 2 million years to reach our first billion. It took us approximately 123 to reach the next.
A mere 33 took us to our third.
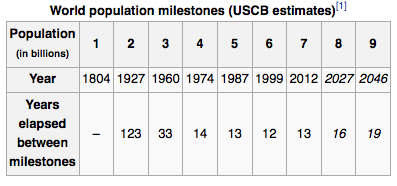
The population gradient for ambient human bodies on Earth.
Prior to around 1800, the most serious human threats to the living planet were deforestation for the sake of construction, war or fuel and maybe wildfires. Secondary to those was mass hunting—particularly the vast atrocities that wiped out entire populations of animals for sport, base ignorance, commerce, or purposes related to human habitation of terrain.
But between the 2nd and 3rd tiers of the human population explosion, new and profusely invasive competitors for resources, attention and terrain were multiplying madly—at rates no one really bothered to examine. During this period, two specific human activity-threats skyrocketed into cultural and ecological dominance, and their impact continues to inscribe a deadly and indelible mark on both human history and terrestrial ecology. I speak here of the machine and the product-for-profit.
Machines are objects against which human beings and living places must directly compete—and we are losing this competition. Inert objects merit more care, attention, valuation, developmental interest, terrain rights, fuel and ‘freedom to reproduce’ than their human originators or the ecologies that are the sources of life and planetary homeostasis. Every living being and place has been subjected to their intrusion, emissions and domination—especially in war. Further, the invention and development of mechanical technology has had profound and unexpected impacts on human development.
Over the past 150 years, Homo Sapiens Sapiens has effectively redirected or even replaced our evolutionary developmental progress in a number of unexpected ways by inhibition, substitution, self-poisoning and, most significantly, by wiping out the ecologies which were the original sources of our evolutionary ascent; standing nearby as both agency of accomplishment and cause we find ‘the machine’.
I would argue that our broad-scale fascination with machines has derailed the development of the intellectual and relational assets necessary to direct our own cultures, let alone the technologies in question, with any degree of insight or wisdom. We have become materialists, and in so doing, we have sounded the death knell of the nurseries of life and intelligence on Earth.
Our extended cultures and collectives are not properly equipped to direct the forces that value, pursue and accomplish technological and industrial development. Our ordinary activities produce results so incredibly ill-considered that were we to pause even briefly in contemplation of them we would prohibit them absolutely. We do not thus pause. Money and the need for it fuel the conversion of the living planet to representations such as cash or goods. And so, too, our human potentials and minds.
It’s murder for money.
Numbers in machines that represent value.
Representations like money arise when what is being represented is no longer available to common experience or expression. As the forests of oral memory were wiped out, we acquired writing. As the experience of the profound value of living beings and places disappeared from common experience, we got a new kind of greenery: cash.
And as cash begins to disappear, we will achieve the ‘third wave’ of re-representation: digital money. Stuff that is not even an object. Nothing more than numbers in machines.
In the case of bitcoin, we are talking about machines that compete against living places and human lives for energy, space, resources, and … attention.
***
Hashing For Cash: Machines Get busy
So, let’s get down to business. What is bitcoin, really? You can think of it as a machine contagion—a network of devices amped to their performance tolerances—machines that do nothing but reprocess every transaction that ever occurred on their network (thus achieving ‘consensus’) while, at the same time, ‘mining’ new blocks of coins (currently worth about 25 btc) by solving a purposefully cumbersome mathematical formula which doesn’t actually accomplish anything other than enforcing computational difficulty. That is: making millions of machines grind away madly at nothing.
This mining process is both the reprocessing of transactions (to join the network), and a ‘weight’ factor that is incremented to insure that the average time for the entire network to ‘solve’ a block (that is, to produce an accurate guess close enough to a mathematically supplied target) is ‘about 10 minutes’.
When you initiate a new machine into the network, you download the current transaction record (a 6-gigabyte file) of the entire history of bitcoin and reprocess it (this takes around 24 hours). You then either ‘mine’ alone (an almost useless endeavor which would take ~98 years to solve a block) or you join a pool of machines. By joining a pool, you get statistically better performance in terms of satoshi (currently: USD $0.0000046543 each) earned as you are ‘rewarded’ for work done by your machine’s participation in the pool.
The more processing power (raw computational force over time) you can bring to bear on ‘the problem’ … the better a chance you have to earn incremental additions to your ‘wallet’ or account. Of course, most of the problem is invented… to be this kind of problem—one that requires more and more computational activity to qualify as complete. And we have now invented specialized machines and chips just to solve this problem.
Machines involved in mining are pressed to the limits of their power consumption and performance profiles; they are ‘pinned’ at 100%+ of their computing power, ceaselessly, and thus generate heat (as well as consuming copious quantities of electrical power).
Because they remain hot, they have to be electronically ventilated. This process of power-heating something we must in turn power-cool, for the phony ‘sake’ of mathematical processes intended to make more work each time they are implemented is deranged. We’re essentially turning computers into heaters that we have to cool to recompute previous computations with. On purpose. A single day of the environmental costs of this process are so catastrophic that if we ever did the accounting — if anyone did — we would immediately understand that this entire idea is a mode of ‘fracking the whole environment’ whose costs rise explosively with every moment we continue the process.
These traditionalists worry that a larger block size will raise the minimum amount of computing power required to fully participate in the Bitcoin network’s peer-to-peer process for clearing transactions. To fully participate in this process, a computer needs to receive a copy of every transaction that has ever been made on the network, which can add up to gigabytes of data every month. If the block limit is raised, then running a Bitcoin node will become even more resource-intensive, potentially pricing out smaller players.
— Ars Magna: A New Deal could End Bitcoin’s Running Civil War
Only a species that had gone entirely insane, and consciously intended to wipe out life on Earth would ever consider such a process. But any species that could actively celebrate and expand it — must be understood as both emphatically suicidal and openly omnicidal. In short: they intend to kill everything, anything, and themselves — and are hell-bent on the continuous and unlimited expansion of this agenda.
The activity of the bitcoin process and some similar networks are not only burning down the future; they are also obliterating the history of humanity and life on Earth, faster and more aggressively every moment, by destroying the living results and opportunities established by this history, and insuring that the benefits that might otherwise blossom into astonishing ‘interest on investment’, are killed off by the necessity of breeding, operating, heating and cooling millions of machines that do makework for a resource that only exists as numbers in machines.
No one with anything resembling a mind would ever allow, let alone celebrate this, and the fact that our modern cultures are doing both is a symptom more serious than our obsessions with war, ecological atrocity, rape-for-profit, and the generation of other lethal processes such as the automobile, the atomic bomb, nuclear reactors and prisons.
bitcoin is an invisible, self-expanding prison/war that, like fracking ‘hides the damage’ in every place and life on Earth. It is a way of violently undermining the very bases of life on Earth, and the fact that no one is doing the accounting is a sign that the social and environmental intelligences of our species have become actively self-compromising.
Imagine if your immune system started producing new forms of HIV instead of macrophages and antibodies… and you begin to get the picture.
Thankfully, there is a limit to the process, but it’s taking a while to get there. The limit is 21 million bitcoins, at least in the present implementation. What does this mean? Well, it means that, according to some sources, 80% of mineable bitcoins will have been acquired within about a year. It also means that the miner margin will shrink, making the process less attractive. It’s not clear what will take place, or if the tail end of this process can be completely accomplished. It’s also not impossible that the present implementation will begin to transform, or reiterate itself once all bitcoins have been mined.
bitcoin forks into two processes 08.01.17.

Money is cached torture, murder, atrocity, and domination. It represents possible transactions in future time by obliterating living beings and opportunities in present time.
The only ‘value’ of the computation thus accomplished is that it leverages statistical complexity against computational power in order to mathematically throttle block (and thus bitcoin) production. So, we are inventing increasing quantities of work for increasing quantities of computers to do and the easier it becomes, the more we throttle it to make it harder… faster.
Purportedly, all of this bother results in profit, at least in theory. I say in theory because the putative returns require investments… of time, space, electricity, temperature, attention… and… computation. What one invests in one way is lost twice, both in the investment and in what more profitable or noble work might have been done with the same effort or resources.
There are a wide variety of other problems here, from the fact that malware that infects vast numbers of machines has been found mining bitcoin (resource diversion), to the embarrassing ‘sudden disappearance’ of thousands (or occasionally millions) of dollars worth of bitcoins in thefts from ‘exchanges’ or technical bungles (wallet loss).
Why are we purchasing banks of highly specialized computers and heating them up with computational burdens that tax their performance spec and then paying to cool them back down—in order to accomplish nothing useful?
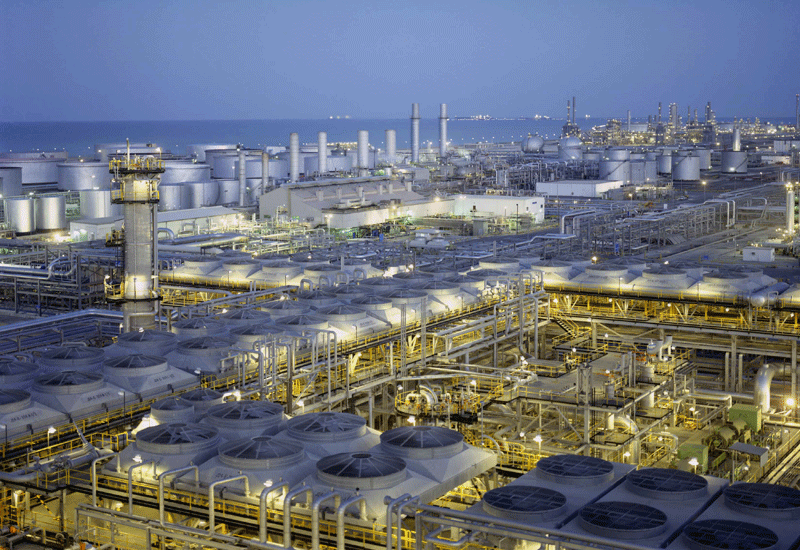
The answer is that we have invented a ‘false problem’ that tens of thousands of machines now work to achieve the result for relatively uninterrupted, and these machines are themselves resources which require resources to build, run, track, back up, and otherwise maintain. How much varies widely by installation, but as you can see in the image that begins this essay, many people are building banks of machines that do nothing but process bitcoin blocks. Nothing else. Just that. And these have to be housed, stored, powered, repaired, attended, backed-up, protected, and cooled.
Bitcoin Energy Usage Analysis.
bitcoin is an essentially mechano-vampiric paradigm where massive amounts of actually usless computation are done with increasing ferocity while producing nothing of any value whatsoever except a kind of pure abstraction of computing having been done, and the glorious ‘record of transactions’ which becomes a veritable church of common computational record—and remains just as meaningless in that guise.
Those who are involved in this racket have chosen to dedicate cash, space, power and other resources to the process. But what is the process? It is to process a meaningless series of processes, ever-more ineffectively, on purpose.
That’s the wrong thing to dedicate resources to, and it produces direct mechanical competition against our own minds, cultures, needs and development. The idea of a homegrown electronic cryptocurrency is not entirely misguided. Personally, I think it would be powerful to develop something that produces value based on merit of actual work, discovery or contribution… accomplished by individuals or collectives. This is something I hope we may see relatively soon. But what bitcoin is and is doing is stridently malformed.
What exactly is profit? A crucial part of the answer is that it is the abstracted remains of obliterated lives, pricelessly irreplaceable ecosystems and precious relationships we never noticed or acknowledged, let alone understood. It is the remains of what might have been revolutionary intelligence, discovery, mutual uplift, evolution, wonder and actual human progress. It is the bodies and remains of animals, human beings and families, dreams of access to new developmental and creative opportunities, and living worlds of possibility that were burnt down and turned into little sheets of paper.
***
In all too many cases, the ‘next big thing’ is actually the next endlessly self-amplifying graveyard.
It is well-known that a ‘materially successful’ male or female represents an attractive mating partner for a variety of reasons, both profound and superficial in nature. In effect, the ‘standing cache’ of a given person or group is a signal about how effective various aspects of their skills and/or intelligence are in the specific domains that these representations are derived from.
The problem is this: the message is mixed, because their cache is social power… but its sources and functions often begin with atrocities,, some of which reach far back into the history of our people and the land.
Bitcoin Block Reward Halving Countdown (many interesting up-to-the-moment statistics about the current state of the process).
Note : There are now a large number of cryptocurrencies, each with unique features, benefits and costs of operation. While some of these may utilize similar processes that require vast amounts of computational activity to generate, others do not. I am presently doing some research to understand more about the other systems, some of which are mentioned in the comments.
Photos: Life inside of China’s massive and remote bitcoin mines
Editor’s note: This article originally appeared on Medium. Republished with permission of the author.